uncover
Running uncover
Learn about running uncover including examples
Basic Usage
For all of the flags and options available for uncover be sure to check out the Usage page. If you have questions, reach out to us through Help.
Default run:
uncover supports multiple ways to make the query including stdin orq flag, as default shodan engine is used for search if no engine is specified.
Single query against multiple search engines
uncover supports multiple search engine, as default shodan is used,-e flag can be used to run same query against any or all search engines.
Multiple queries against multiple search engines
Shodan-InternetDB API
uncover supports shodan-internetdb API to pull available ports for given IP/CIDR input.shodan-idb used as default engine when IP/CIDR is provided as input, otherwise shodan search engine is used.
Awesome Search Queries Integration
The-asq, -awesome-search-queries flag allows you to use predefined awesome search queries to discover exposed assets on the internet. This feature leverages a curated list of queries that are known to yield interesting results. To use this feature, simply specify the -asq flag followed by the desired query. For example, to search for exposed Jira instances, you can use:
Field Format
-f, -field flag can be used to indicate which fields to return, currently, ip, port, and host are supported and can be used to return desired fields.
Field Formatting
uncover has a-f, -field flag that can be used to customize the output format. For example, in the case of uncover -f https://ip:port/version, ip:port will be replaced with results in the output while keeping the format defined, It can also be used to specify a known scheme/path/file in order to prepare the output so that it can be immediately passed as input to other tools in the pipeline.
uncover -q example -f ip | naabu- Runs naabu for port scanning on the found host.uncover -q title:GitLab | httpx- Runs httpx for web server probing the found result.uncover -q 51.83.59.99/24 | httpx- Runs httpx on host/ports obtained from shodan-internetdb.
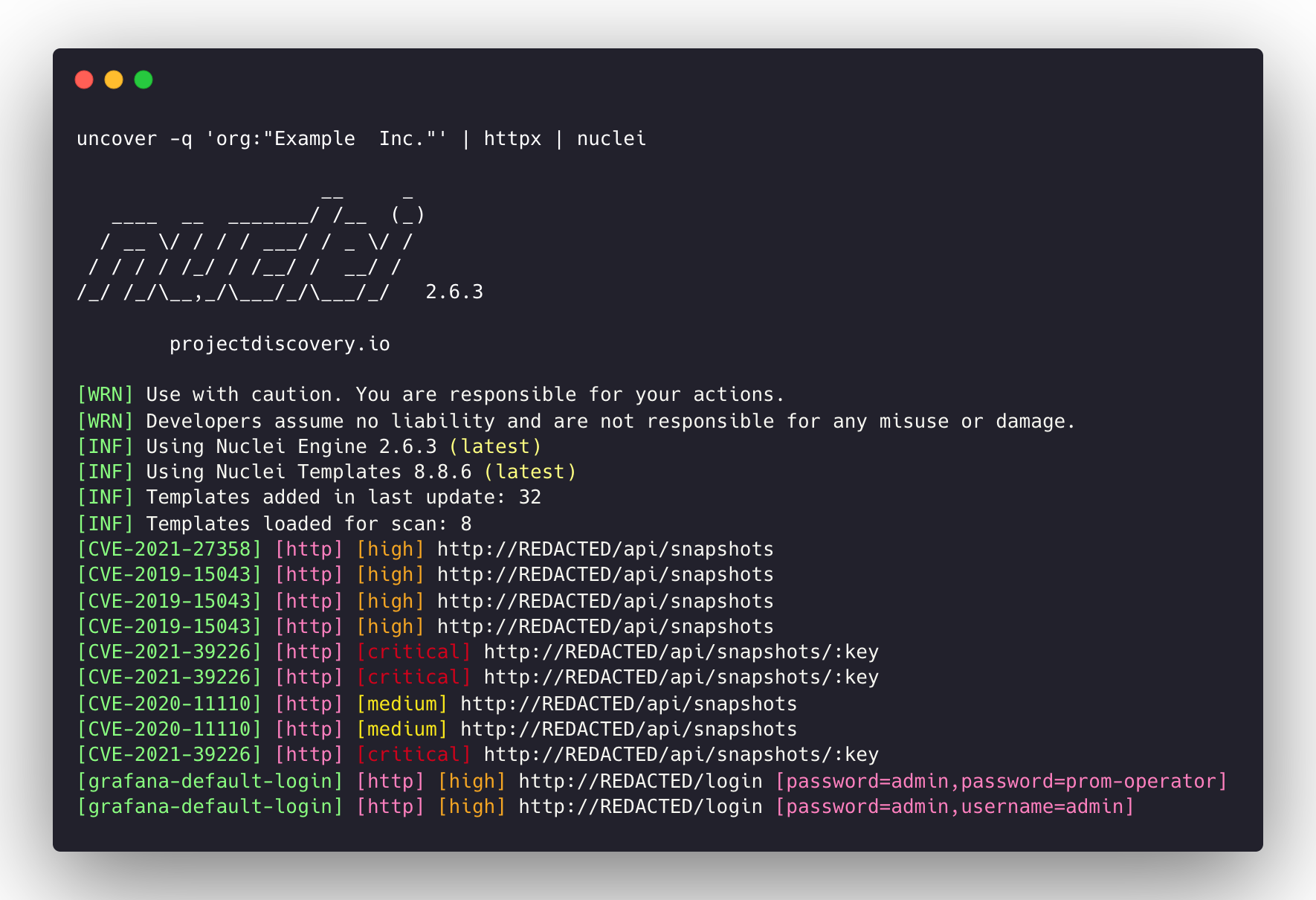
uncover -q 'org:"Example Inc."' | httpx | nuclei- Runs httpx / nuclei for vulnerability assessment.