Slack
MS Teams
Webhook
Jira
GitHub
GitLab
Linear
AWS
GCP
Azure
Alibaba
Kubernetes
Cloudflare
Fastly
DigitalOcean
Notification Integrations
Alerting integrations support notifications as part of scanning and asset discovery, and include Slack, Microsoft Teams, Email, and custom Webhooks. Navigate to Scans → Configurations → Alerting to configure your alerts.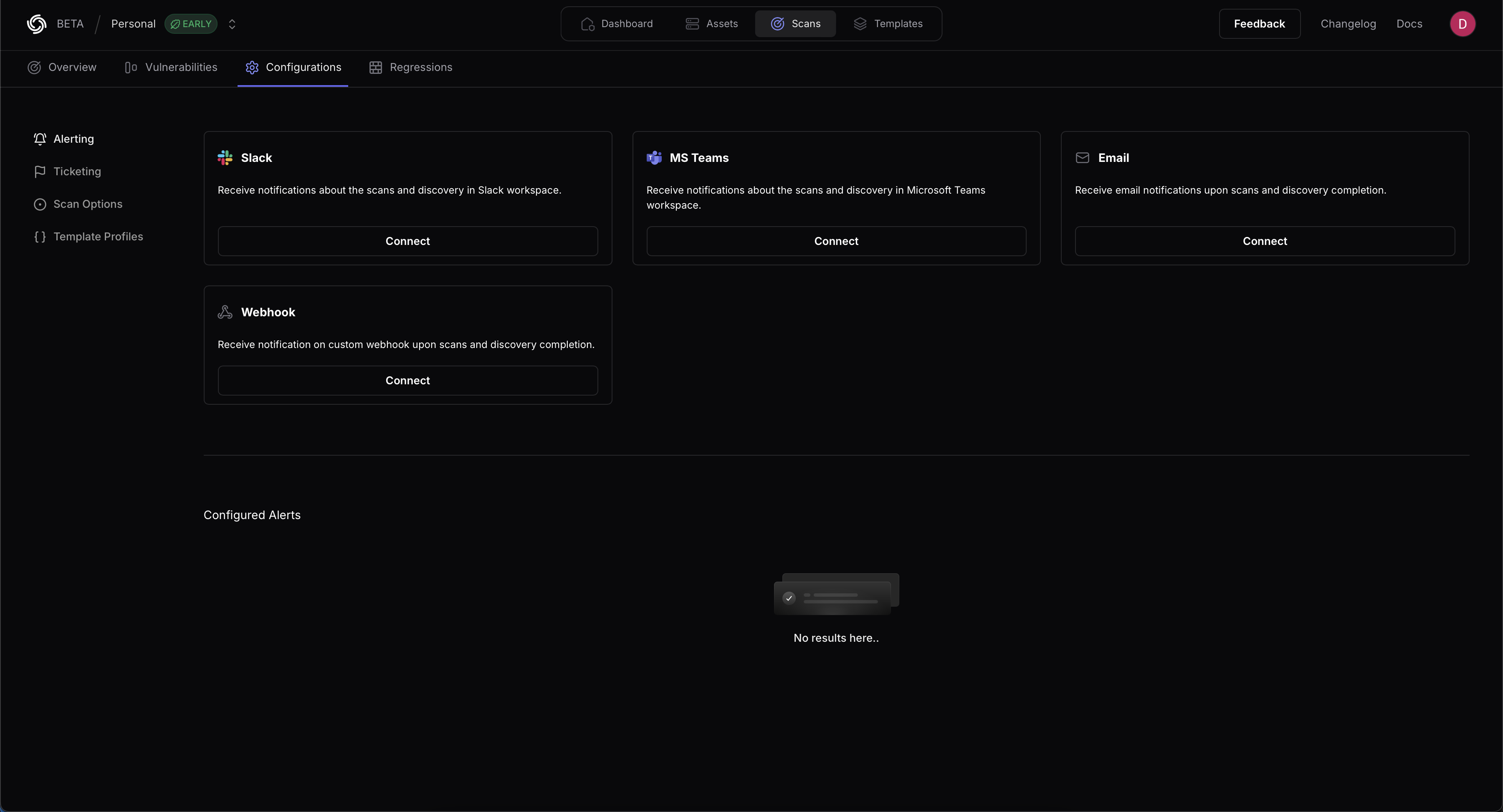
Slack
ProjectDiscovery supports scan notifications through Slack. To enable Slack notifications provide a name for your Configuration, a webhook, and an optional username. Choose from the list of Events (Scan Started, Scan Finished, Scan Failed) to specify what notifications are generated. All Events are selected by default- Refer to Slack’s documentation on creating webhooks for configuration details.
MS Teams
ProjectDiscovery supports notifications through Microsoft Teams. To enable notifications, provide a name for your Configuration and a corresponding webhook. Choose from the list of Events (Scan Started, Scan Finished, Scan Failed) to specify what notifications are generated.- Refer to Microsoft’s documentation on creating webhooks for configuration details.
Webhook
ProjectDiscovery supports custom webhook notifications, allowing you to post events to any HTTP endpoint that matches your infrastructure requirements.Quick Setup
- Navigate to Scans → Configurations → Alerting
- Select “Webhook” integration
- Provide your endpoint URL and optional authentication
- Choose which events to receive (New Asset, New Vulnerability, Scan/Asset Finished/Failed)
- Select severity filters (optional)
A descriptive name for your webhook configuration
Your HTTPS endpoint that will receive POST requestsExample:
https://your-domain.com/api/security/alertsEvent Types Overview
ProjectDiscovery sends webhook notifications as HTTP POST requests withContent-Type: application/json. Each scan or enumeration job triggers multiple webhooks throughout its lifecycle.
Scan Events
Track vulnerability scan lifecycle from start to completion
Discovery Events
Monitor asset discovery operations in real-time
New Vulnerability
Alerts when new vulnerabilities are found (rescans only)
New Asset
Alerts when new assets are discovered in your attack surface
Webhook Payload Reference
- Scan Events
- Discovery Events
- New Asset / Vulnerability Events
Select a scan event to view its webhook payload structure:
Scan Started
Scan Started
Trigger: Immediately when a vulnerability scan begins executionType:
runningScan Started Payload
Field Definitions
Field Definitions
Root Fields:
type— Always"running"for this eventmessage— Human-readable status messagescan_name— Name of the scan configurationscan_id— Unique identifier for this scan execution
started_at— ISO 8601 timestamp when scan startedtotal_targets— Number of targets to scan (integer)total_templates— Number of templates being used (integer)total_requests— Estimated total HTTP requests (integer)
Scan Finished
Scan Finished
Trigger: When a vulnerability scan completes successfullyType:
finishedScan Finished Payload
Field Definitions
Field Definitions
Root Fields:
type— Always"finished"for this eventmessage— Human-readable status messagescan_name— Name of the scan configurationscan_id— Unique identifier for this scan execution
finished_at— ISO 8601 timestamp when scan completedscan_time— Total duration in seconds (e.g., “4500s”)total_matches— Total vulnerabilities found (integer)severity_breakdown— Count by severity level (object)critical— Critical severity counthigh— High severity countmedium— Medium severity countlow— Low severity countinfo— Info severity count
rescan_new_vulnerabilities— New vulns since last scan, rescans only (integer)rescan_vulns_list— List of new vulnerabilities, max 15 items, rescans only (array)Name— Vulnerability name/titleSeverity— Severity level (critical, high, medium, low, info)Count— Number of instances found
Scan Failed
Scan Failed
Trigger: When a scan fails or is manually stoppedType:
failed_stoppedScan Failed Payload
Field Definitions
Field Definitions
Root Fields:
type— Always"failed_stopped"for this eventmessage— Human-readable status messagescan_name— Name of the scan configurationscan_id— Unique identifier for this scan execution
timestamp— ISO 8601 timestamp when failure occurredprogress— Completion percentage (0-100) when failed (integer)failure_reason— Description of why scan failed or was stopped (string)
Ticketing Integrations
The integrations under Ticketing support ticketing functionality as part of scanning and include support for Jira, GitHub, GitLab, and Linear. Navigate to Scans → Configurations → Ticketing to configure your ticketing tools.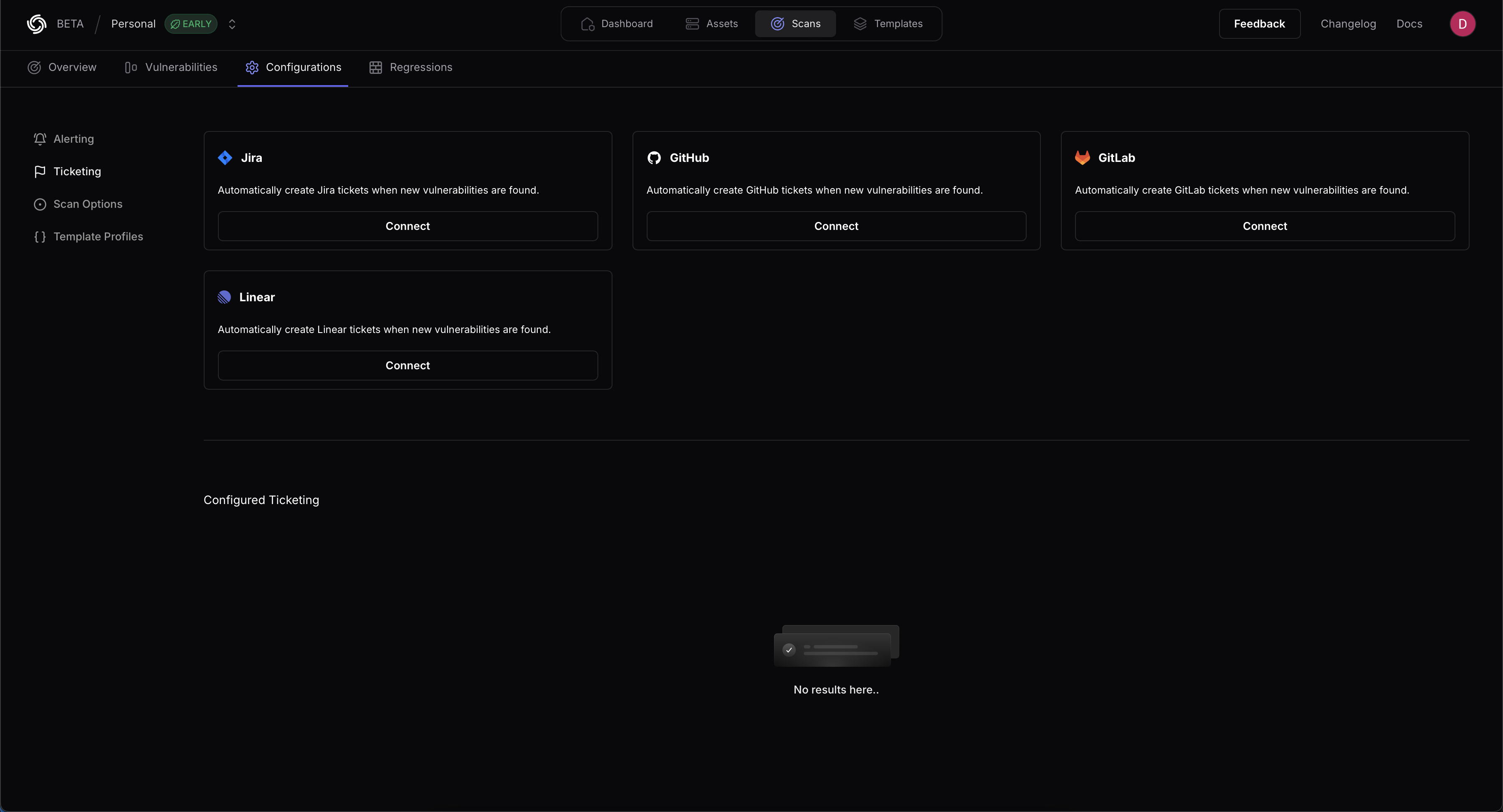
Jira
ProjectDiscovery provides integration support for Jira to create new tickets when vulnerabilities are found. Provide a name for the configuration, the Jira instance URL , the Account ID, the Email, and the associated API token. Details on creating an API token are available in the Jira documentation here.GitHub
ProjectDiscovery provides integration support for GitHub to create new tickets when vulnerabilities are found. Provide a name for the configuration, the Organization or username, Project name, Issue Assignee, Token, and Issue Label. The Issue Label determines when a ticket is created. (For example, if critical severity is selected, any issues with a critical severity will create a ticket.)- The severity as label option adds a template result severity to any GitHub issues created.
- Deduplicate posts any new results as comments on existing issues instead of creating new issues for the same result.
GitLab
ProjectDiscovery provides integration support for GitLab to create new tickets when vulnerabilities are found. Provide your GitLab username, Project name, Project Access Token and a GitLab Issue label. The Issue Label determines when a ticket is created. (For example, if critical severity is selected, any issues with a critical severity will create a ticket.)- The severity as label option adds a template result severity to any GitLab issues created.
- Deduplicate posts any new results as comments on existing issues instead of creating new issues for the same result.
Linear
ProjectDiscovery integrates with Linear for automated issue tracking. The integration requires the following API parameters:- Linear API Key
- Linear Team ID
- Linear Open State ID
- API Key Generation:
- Path: Linear > Settings > API > Personal API keys
- Direct URL: linear.app/[workspace]/settings/api
- Team ID Retrieval:
- Open State ID Retrieval:
Cloud Asset Discovery
ProjectDiscovery supports integrations with all popular cloud providers to automatically sync externally facing hosts for vulnerability scanning. This comprehensive approach ensures all your cloud resources with external exposure are continuously monitored, complementing our external discovery capabilities. The result is complete visibility of your attack surface across cloud environments through a simple web interface.AWS (Amazon Web Services)
Configure AWS Integration
Click here to open the AWS integration configuration page in the ProjectDiscovery Cloud platform
| Service | Description |
|---|---|
| EC2 | VM instances and their public IPs |
| Route53 | DNS hosted zones and records |
| S3 | Buckets (especially those public or with DNS) |
| Cloudfront | CDN distributions and their domains |
| ECS | Container cluster resources |
| EKS | Kubernetes cluster endpoints |
| ELB | Load balancers (Classic ELB and ALB/NLB) |
| ELBv2 | Load balancers (Classic ELB and ALB/NLB) |
| Lambda | Serverless function endpoints |
| Lightsail | Lightsail instances (simplified VPS) |
| Apigateway | API endpoints deployed via Amazon API Gateway |
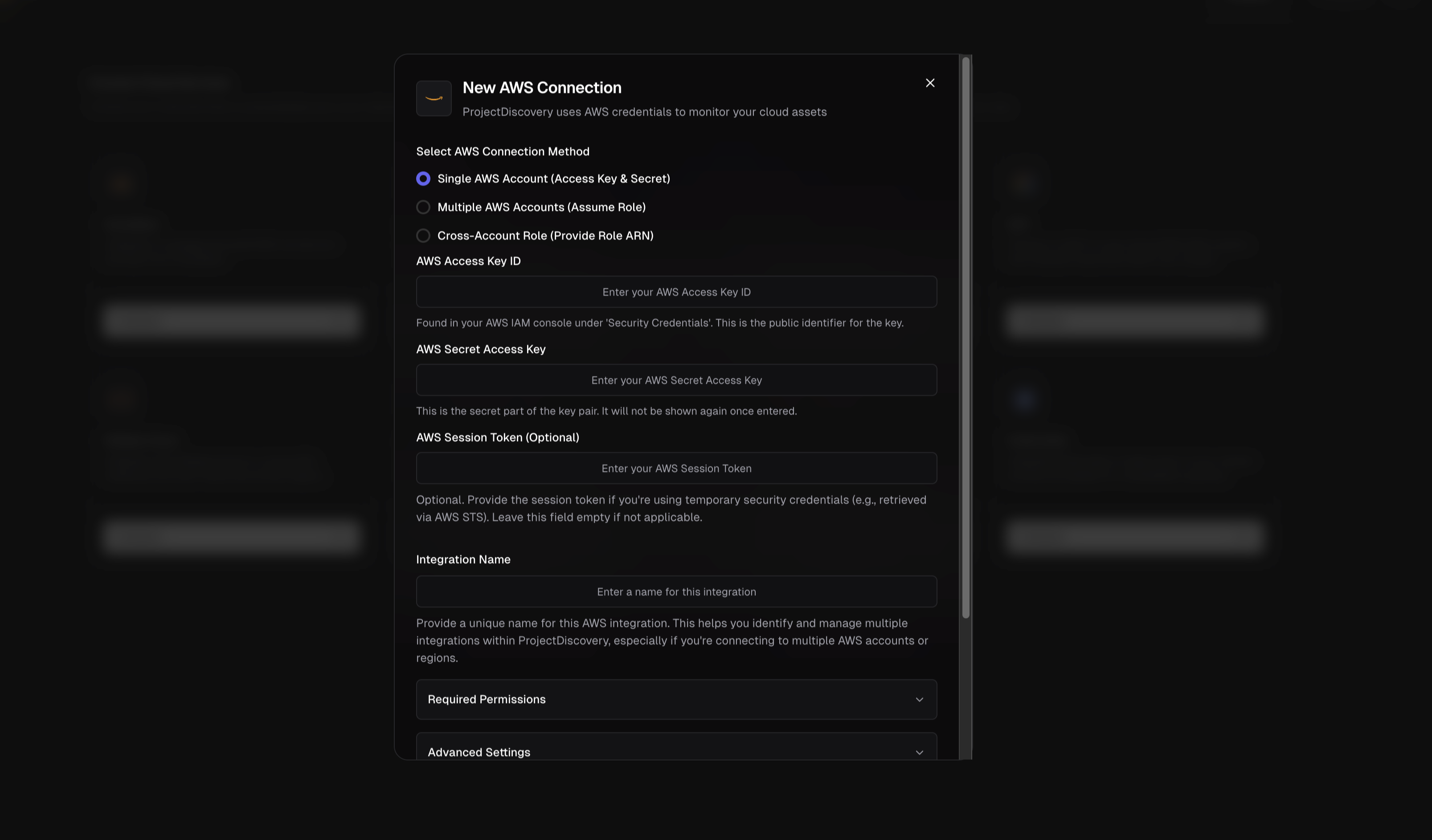
- Single AWS Account (Access Key & Secret) – Direct credential-based authentication using an IAM User’s Access Key ID and Secret Access Key to connect one AWS account. Choose this for quick setups or single-account monitoring.
- Multiple AWS Accounts (Assume Role) – Use one set of credentials to assume roles in multiple accounts. This method is ideal for organizations with multiple AWS accounts (e.g. dev, prod, etc.). You provide one account’s credentials and the common role name that exists in all target accounts.
- Cross-Account Role (Role ARN) – Use a dedicated IAM role with an External ID for third-party access. This option lets you create a cross-account IAM role in your AWS account and grant ProjectDiscovery access via that role’s Amazon Resource Name (ARN). This is the most secure integration method, as it follows AWS best practices for third-party account access.
- AWS Account – Access to an AWS account where you can create IAM identities
- Admin Access to IAM – Permissions to create IAM users and roles
- ProjectDiscovery Account – Access to ProjectDiscovery’s Cloud platform
- Basic AWS IAM Knowledge – Understanding of IAM users, access keys, and roles
1. Single AWS Account (Access Key & Secret)
To connect a single AWS account directly:- Create a Read-Only IAM User: In the AWS IAM console, create a new IAM user for ProjectDiscovery integration. Assign programmatic access (which generates an Access Key ID and Secret Access Key).
- Attach Required Policies: Grant the user read-only permissions to the AWS services you want to monitor. You can use AWS-managed policies like AmazonEC2ReadOnlyAccess, AmazonS3ReadOnlyAccess, etc. for each service (see the Required Permissions section below).
- Configure in ProjectDiscovery:
- Select Single AWS Account (Access Key & Secret)
- Enter your AWS Access Key ID and AWS Secret Access Key
- Optionally provide a Session Token (only for temporary credentials)
- Give the integration a unique name
- Select the AWS services you want to monitor
2. Multiple AWS Accounts (Assume Role)
For monitoring multiple AWS accounts from a central account:- Choose a Primary Account: Create an IAM user in one AWS account (the “primary”) with programmatic access.
- Create an IAM Role in Each Target Account: In each AWS account you want to monitor, create a role that:
- Uses the same role name across all accounts (e.g., “ProjectDiscoveryReadOnlyRole”)
- Has a trust relationship allowing your primary account to assume it
- Has the required read-only permissions
- Configure in ProjectDiscovery:
- Select Multiple AWS Accounts (Assume Role)
- Enter the primary account’s AWS Access Key ID and Secret Access Key
- Specify the Role Name to Assume (the common role name)
- List all AWS Account IDs to monitor (one per line)
- Give the integration a unique name
- Select the AWS services you want to monitor
3. Cross-Account Role (Role ARN)
The most secure method using ProjectDiscovery’s service account:- Create an IAM Role in Your AWS Account:
- In your AWS console, go to IAM → Roles → Create Role
- Select “Another AWS account” as the trusted entity
- Enter ProjectDiscovery’s ARN:
arn:aws:iam::034362060511:user/projectdiscovery - Enable “Require External ID” and enter the External ID shown in the ProjectDiscovery UI
- Attach the necessary read-only permissions
- Configure in ProjectDiscovery:
- Select Cross-Account Role (Role ARN)
- Enter the Role ARN of the role you created
- Give the integration a unique name
- Select the AWS services you want to monitor
- EC2 - AmazonEC2ReadOnlyAccess
- Route53 - AmazonRoute53ReadOnlyAccess
- S3 - AmazonS3ReadOnlyAccess
- Lambda - AWSLambda_ReadOnlyAccess
- ELB - ElasticLoadBalancingReadOnly
- Cloudfront - CloudFrontReadOnlyAccess
- Check Asset Discovery: In the ProjectDiscovery platform, navigate to the cloud assets or inventory section. After a successful integration, you should start seeing resources from your AWS account(s) listed (for example, EC2 instance IDs, S3 bucket names, etc., corresponding to the integrated accounts). It may take a short while for the initial discovery to complete. If you see those assets, the integration is working.
- Test with a Known Resource: As a quick test, pick a known resource (like a specific EC2 instance or S3 bucket in your AWS account) and search for it in ProjectDiscovery’s asset inventory. If it appears, the connection is functioning and pulling data.
- Troubleshooting Errors: If the integration fails or some assets are missing, consider these common issues:
- Incorrect Credentials: Double-check that the Access Key and Secret (if used) were entered correctly and correspond to an active IAM user. If you recently created the user, ensure you copied the keys exactly (no extra spaces or missing characters).
- Insufficient Permissions: If certain services aren’t showing up, the IAM policy might be missing permissions. For example, if S3 buckets aren’t listed, confirm that the policy includes
s3:ListAllMyBuckets. Refer back to the Required Permissions and make sure all relevant actions are allowed. You can also use AWS IAM Policy Simulator or CloudTrail logs to see if any AccessDenied errors occur when ProjectDiscovery calls AWS APIs. - Assume Role Failures: In multi-account or cross-account setups, a common issue is a misconfigured trust relationship. If ProjectDiscovery cannot assume a role, you might see an error in the UI or logs like “AccessDenied: Not authorized to perform sts:AssumeRole”. In that case, check the following:
- The trust policy of the IAM role (in target account) trusts the correct principal (either your primary account’s IAM user/role ARN for multi-account, or ProjectDiscovery’s external account ID for cross-account) and the External ID if applicable.
- The role name or ARN in the ProjectDiscovery config exactly matches the one in AWS (spelling/case must match).
- The primary credentials (for multi-account) have permission to call
AssumeRole.
- External ID Mismatch: For cross-account roles, if the external ID in ProjectDiscovery and the one in the IAM role’s trust policy do not match, AWS will deny the assume request. Ensure you didn’t accidentally copy the wrong value or include extra spaces. It must be exact.
- AWS CloudTrail Logs: As an additional verification, you can check AWS CloudTrail in your account. When ProjectDiscovery connects, you should see events like
DescribeInstances,ListBuckets, etc., being called by the IAM user or assumed role. For cross-account roles, you will see anAssumeRoleevent from ProjectDiscovery’s AWS account ID, and subsequent calls under the assumed role’s identity. This audit trail can confirm that the integration is working as intended and using only allowed actions.
- https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_examples_iam_read-only-console.html
- https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html
- https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_request.html
- https://docs.aws.amazon.com/sdkref/latest/guide/feature-assume-role-credentials.html
- https://docs.logrhythm.com/OCbeats/docs/aws-cross-account-access-using-sts-assume-role
Google Cloud Platform (GCP)
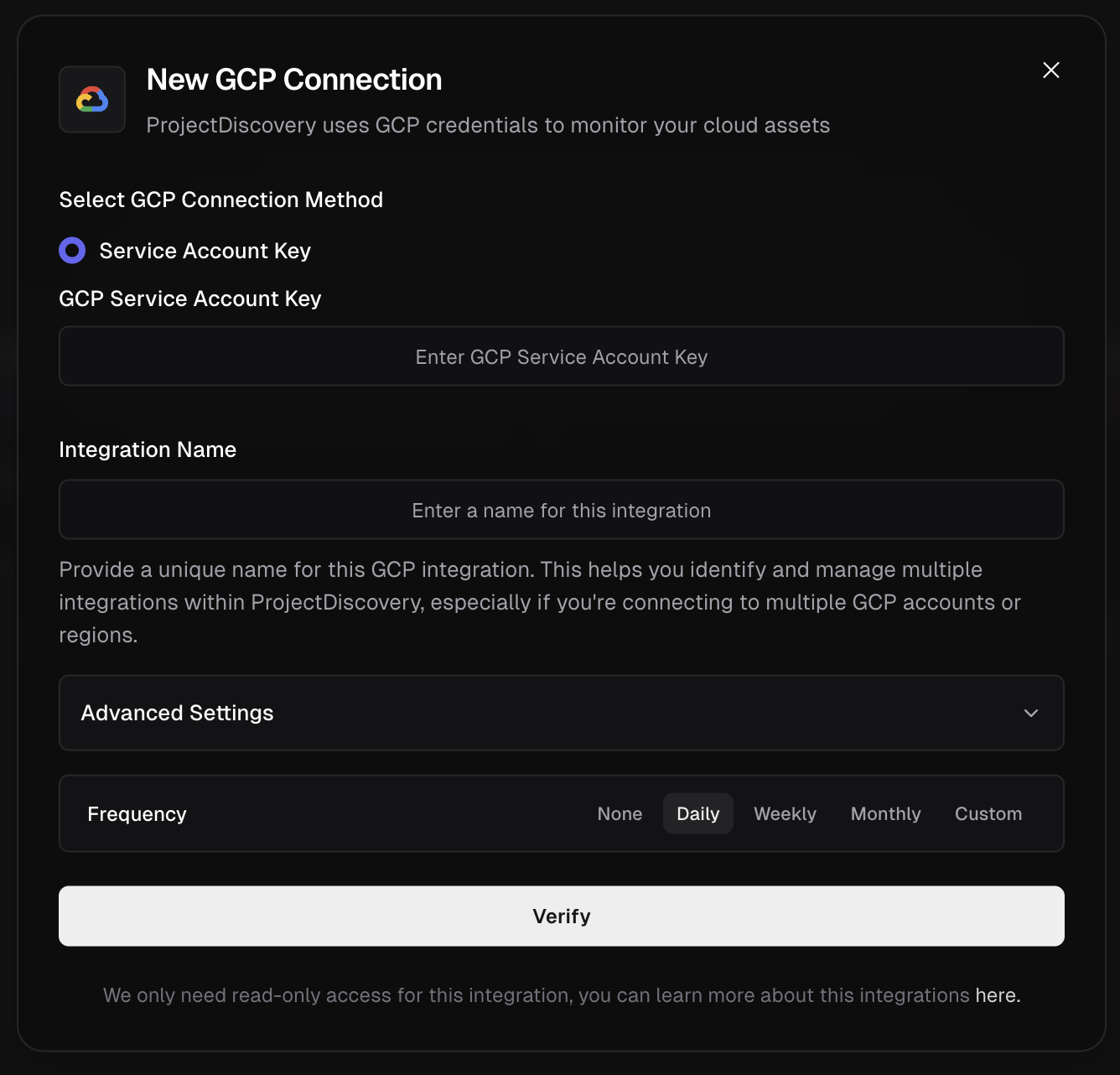
Configure GCP Integration
Click here to open the GCP integration configuration page in the ProjectDiscovery Cloud platform
-
Organization-Level Asset API (Recommended for Enterprises)
- Uses Google Cloud’s Asset Inventory API for comprehensive organization-wide discovery
- Discovers assets across entire GCP organization with a single configuration
- Requires organization-level permissions:
roles/cloudasset.viewerandroles/resourcemanager.viewer - Ideal for large organizations with multiple projects
-
Individual Service APIs (Default)
- Uses individual GCP service APIs for project-specific discovery
- Faster execution with detailed resource metadata
- Requires project-level permissions for each service
- Ideal for focused, single-project discovery
Multi-Organization Support
ProjectDiscovery supports monitoring multiple GCP organizations simultaneously. Simply configure multiple integrations with different organization IDs to get consolidated asset discovery across all your GCP environments (e.g., production, staging, development organizations).Finding Your Organization ID
-
Via Google Cloud Console:
- Go to the Google Cloud Console
- In the top navigation, click on the project selector (next to “Google Cloud Platform”)
- Click All tab to view all resources
- Look for your organization name - the Organization ID is displayed next to it
- Alternatively, go to IAM & Admin > Settings - your Organization ID will be shown at the top
-
Via gcloud CLI:
-
Via Organization Policies Page:
- Navigate to Organization Policies in the Console
- Your Organization ID will be displayed in the URL and page header
Checking Your Permissions
Before setting up the integration, verify you have the necessary permissions:-
For Organization-Level Integration:
-
For Project-Level Integration:
Step-by-Step Setup Instructions
Option 1: Organization-Level Asset API Setup
-
Verify Organization Access:
- Ensure you have
roles/cloudasset.viewerandroles/resourcemanager.viewerat the organization level - You can check this in IAM & Admin > IAM by switching to your organization scope
- Ensure you have
-
Create Service Account:
- Navigate to any project within your organization
- Go to IAM & Admin > Service Accounts
- Click Create Service Account
- Name it something like
projectdiscovery-org-scanner - Click Create and Continue
-
Grant Organization-Level Permissions:
- Go to IAM & Admin > IAM
- Switch to your Organization scope (not project)
- Click Grant Access
- Enter your service account email:
projectdiscovery-org-scanner@YOUR_PROJECT_ID.iam.gserviceaccount.com - Assign these roles:
Cloud Asset ViewerOrganization Viewer
- Click Save
-
Generate Service Account Key:
- Return to Service Accounts
- Click on your service account
- Go to Keys tab
- Click Add Key > Create New Key
- Choose JSON format
- Download and securely store the key file
Option 2: Individual Service APIs Setup
-
Select Target Project:
- Choose the specific project you want to monitor
- Note the Project ID (not the display name)
-
Create Service Account:
- Navigate to IAM & Admin > Service Accounts in your target project
- Click Create Service Account
- Name it something like
projectdiscovery-scanner - Click Create and Continue
-
Grant Project-Level Permissions:
- On the same page, assign these roles:
Compute ViewerDNS ReaderStorage Object ViewerCloud Run ViewerCloud Functions ViewerKubernetes Engine ViewerBrowser(for basic project access)
- Click Continue and then Done
- On the same page, assign these roles:
-
Generate Service Account Key:
- Click on your service account
- Go to Keys tab
- Click Add Key > Create New Key
- Choose JSON format
- Download and securely store the key file
- https://cloud.google.com/iam/docs/service-account-overview
- https://cloud.google.com/iam/docs/keys-create-delete#creating
- https://cloud.google.com/asset-inventory/docs/overview
Azure
Configure Azure Integration
Click here to open the Azure integration configuration page in the ProjectDiscovery Cloud platform
- Virtual Machines
- Public IP Addresses
- Traffic Manager
- Storage Accounts
- Azure Kubernetes Service (AKS)
- Content Delivery Network (CDN)
- DNS Zones and Records
- Application Gateway & Load Balancer
- Container Instances
- App Service & Web Apps
- Azure Functions
- API Management
- Front Door
- Container Apps
- Static Web Apps
Quick Setup Options
For most users (Service Principal method): Create an App Registration in Azure Active Directory with the following required credentials:- Azure Tenant ID
- Azure Subscription ID
- Azure Client ID
- Azure Client Secret
- Create App Registration:
- Go to Azure Active Directory > App registrations > + New registration.
- From the app’s Overview page, collect the Application (client) ID and Directory (tenant) ID.
- Generate Client Secret:
- In the app, navigate to Certificates & secrets > + New client secret.
- CRITICAL: Copy the secret Value immediately, as it is shown only once.
- Assign Permissions:
- Go to your Subscription > Access control (IAM).
- Prefer a least-privilege custom role instead of the broad built-in Reader.
- Create a custom role (for example, “CloudList Reader”) with minimal actions and then assign it to the App Registration you created. Example definition:
- If you only need specific services, you can further reduce actions. For example:
- Virtual machines:
Microsoft.Compute/virtualMachines/read, plus RG/subscription reads - Public IPs:
Microsoft.Network/publicIPAddresses/read - Traffic Manager:
Microsoft.Network/trafficManagerProfiles/read - Storage Accounts:
Microsoft.Storage/storageAccounts/read - AKS Clusters:
Microsoft.ContainerService/managedClusters/read - CDN:
Microsoft.Cdn/profiles/read,Microsoft.Cdn/profiles/endpoints/read - DNS:
Microsoft.Network/dnszones/read,Microsoft.Network/dnszones/recordsets/read - App Services:
Microsoft.Web/sites/read - Functions:
Microsoft.Web/sites/functions/read - Container Apps:
Microsoft.App/containerApps/read
- Virtual machines:
- After creating the role, assign it to the App Registration under Role assignments.
- Alternatively, if creating custom roles is not feasible in your environment, you may assign the built-in Reader role to the App Registration. This provides broader read access across the subscription and may exceed least-privilege needs.
- Note your Subscription ID from the subscription’s overview page.
- Connect:
- Enter the four collected credentials (Tenant ID, Client ID, Client Secret, and Subscription ID) into ProjectDiscovery Cloud Platform to configure the integration.
- https://docs.microsoft.com/en-us/azure/active-directory/develop/howto-create-service-principal-portal
- https://learn.microsoft.com/en-us/azure/role-based-access-control/custom-roles-portal
- https://learn.microsoft.com/en-us/azure/active-directory/develop/app-objects-and-service-principals
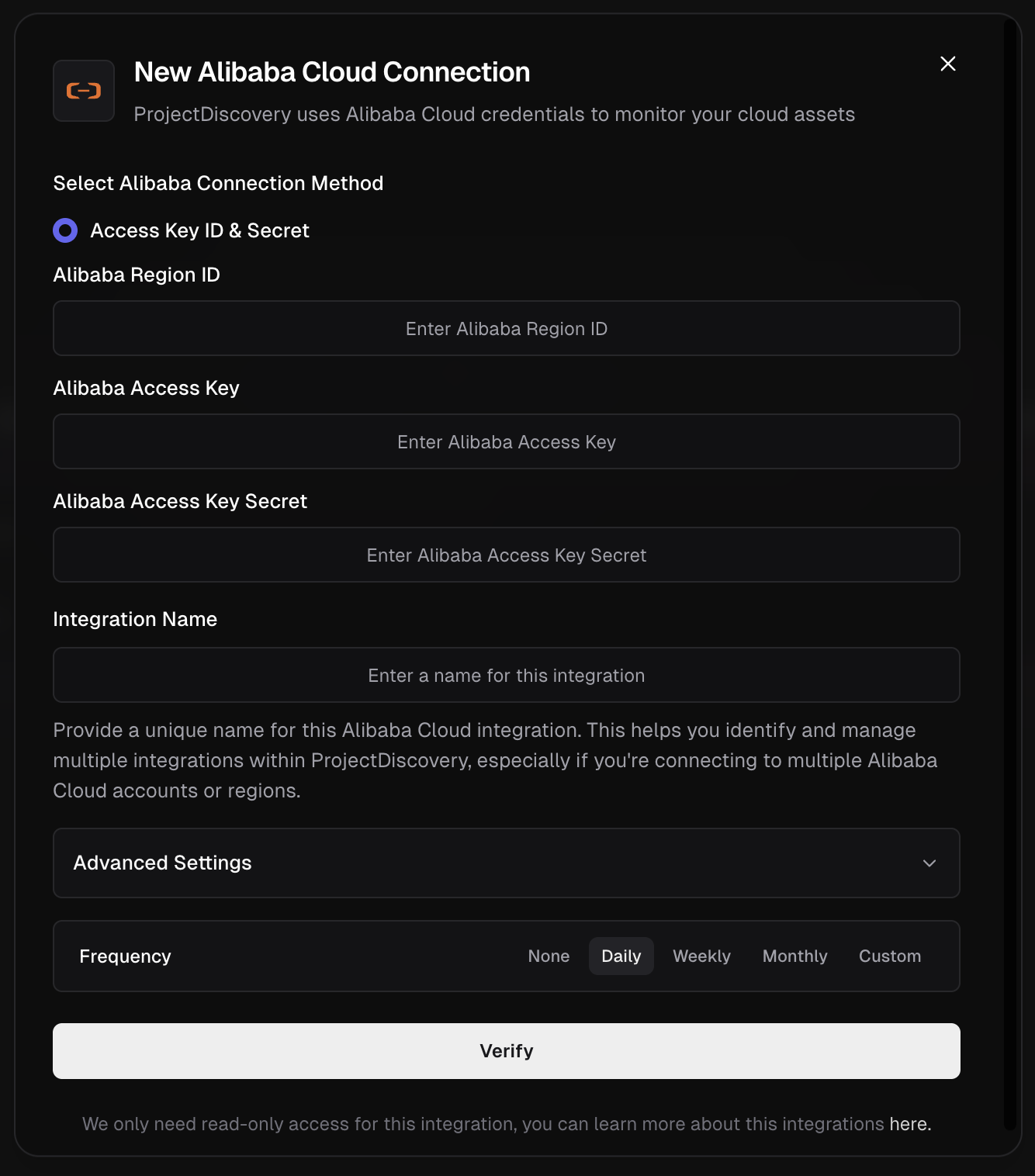
Alibaba Cloud
Configure Alibaba Cloud Integration
Click here to open the Alibaba Cloud integration configuration page in the ProjectDiscovery Cloud platform
- ECS Instances
-
Create a RAM User for API Access:
- Navigate to the RAM (Resource Access Management) console. Ref
- From the left menu, go to Identities > Users and click Create User.
- Enter a Logon Name (e.g.,
projectdiscovery-readonly). - For Access Mode, select OpenAPI Access and click OK. This is for programmatic access, not console login.
-
Securely Store the Access Key: An AccessKey pair is generated immediately after the user is created. This is the only time the secret is shown.
On the confirmation screen, copy the AccessKey ID and the AccessKey Secret. Store them in a secure location immediately. The secret cannot be retrieved after you close this dialog.
-
Grant Read-Only Permissions:
- Return to the Users list.
- Find the user you just created and click Add Permissions in the Actions column.
- Select the System Policy type.
- Search for and select the
AliyunReadOnlyAccesspolicy and click OK. This is the official, managed policy for read-only access to all cloud resources.
-
Find Your Region ID and Connect:
- Identify the Region ID for the resources you plan to monitor. You can find the official list in the Alibaba Cloud documentation here: Regions and zones (This link lists the specific IDs required for API configuration).
- Use the credentials you have collected to fill in the fields in ProjectDiscovery:
- Alibaba Region ID: The target region, for example,
us-east-1. - Alibaba Access Key: The AccessKey ID from Step 2.
- Alibaba Access Key Secret: The AccessKey Secret from Step 2.
- Alibaba Region ID: The target region, for example,
- Enter a unique Integration Name and click Verify.
- https://www.alibabacloud.com/help/faq-detail/142101.htm
- https://www.alibabacloud.com/help/doc-detail/53045.htm
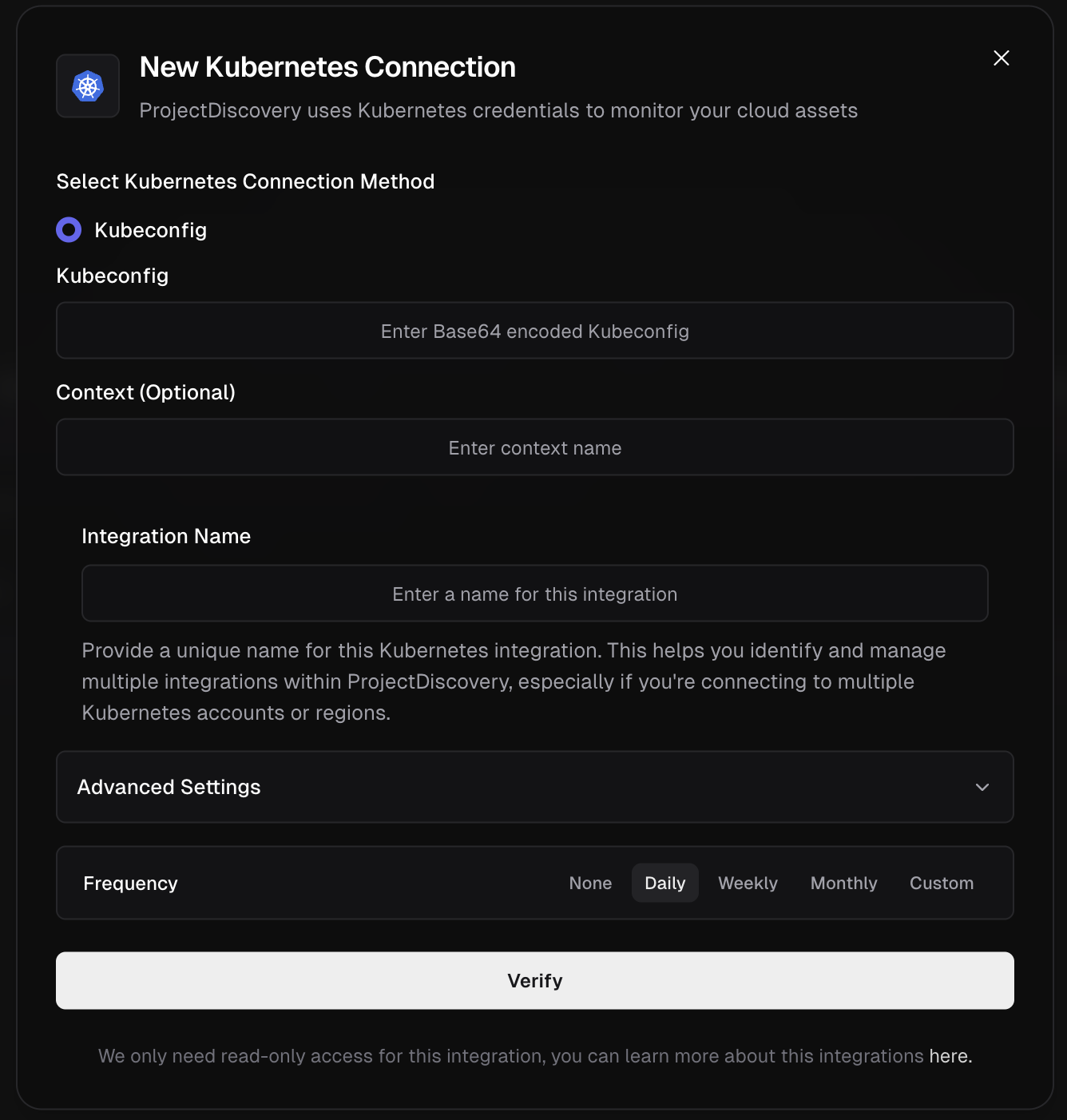
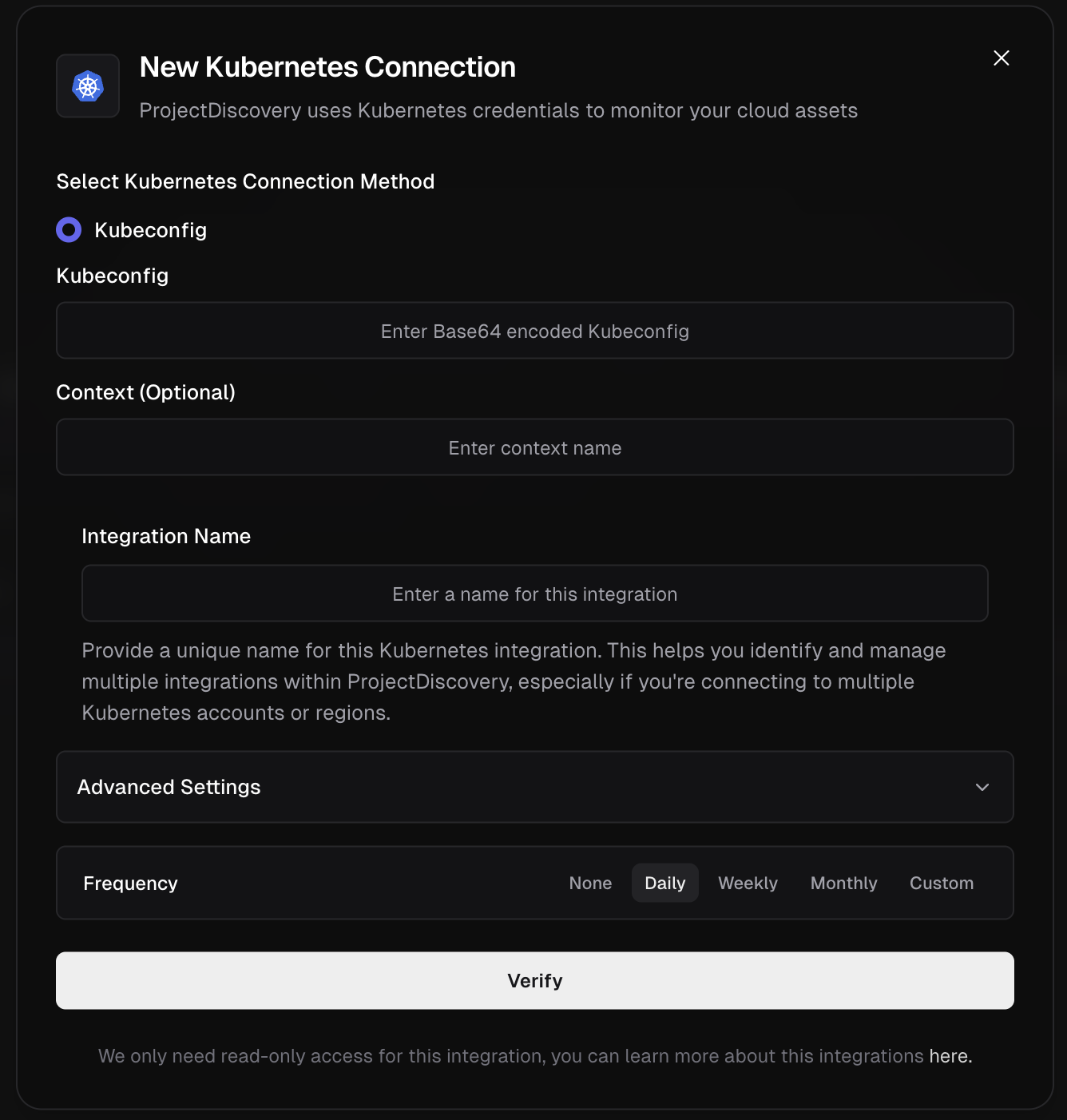
Kubernetes
Configure Kubernetes Integration
Click here to open the Kubernetes integration configuration page in the ProjectDiscovery Cloud platform
- Services
- Ingresses
- Cross-cloud cluster discovery
Cluster Accessibility: Before attempting integration, ensure your Kubernetes cluster has public/external endpoints that ProjectDiscovery can access. This includes:
- Publicly accessible API servers
- External load balancers exposing services
- Internet-facing ingress controllers
- Clusters with public IP addresses
-
Prepare Base64-Encoded Kubeconfig
-
Your kubeconfig file is typically located at:
-
Encode it using:
-
Paste the output into the Kubeconfig field in the UI.
⚠️ Ensure the entire content is copied without extra whitespace.
-
Your kubeconfig file is typically located at:
-
Specify Context (Optional)
-
If your kubeconfig has multiple contexts, find them with:
-
To view the current context:
- Use the relevant context name if required.
-
If your kubeconfig has multiple contexts, find them with:
- Define Integration Name & Verify Choose a unique, descriptive name for this integration and click Verify to complete the integration.
- Internal Clusters: Clusters only accessible within private networks (VPN, internal VPCs) cannot be reached by ProjectDiscovery
- Firewall Restrictions: Ensure your cluster’s API server and services are accessible from the internet
- Network Policies: Check that network policies allow external access to required endpoints
- Load Balancer Configuration: Verify that external load balancers are properly configured and accessible
Alternative for Internal Clusters: For internal-only Kubernetes clusters, consider using the cloud provider integration (AWS EKS, GCP GKE, Azure AKS) which can discover cluster endpoints through the cloud provider’s APIs, or manually add the cluster’s external endpoints as assets.
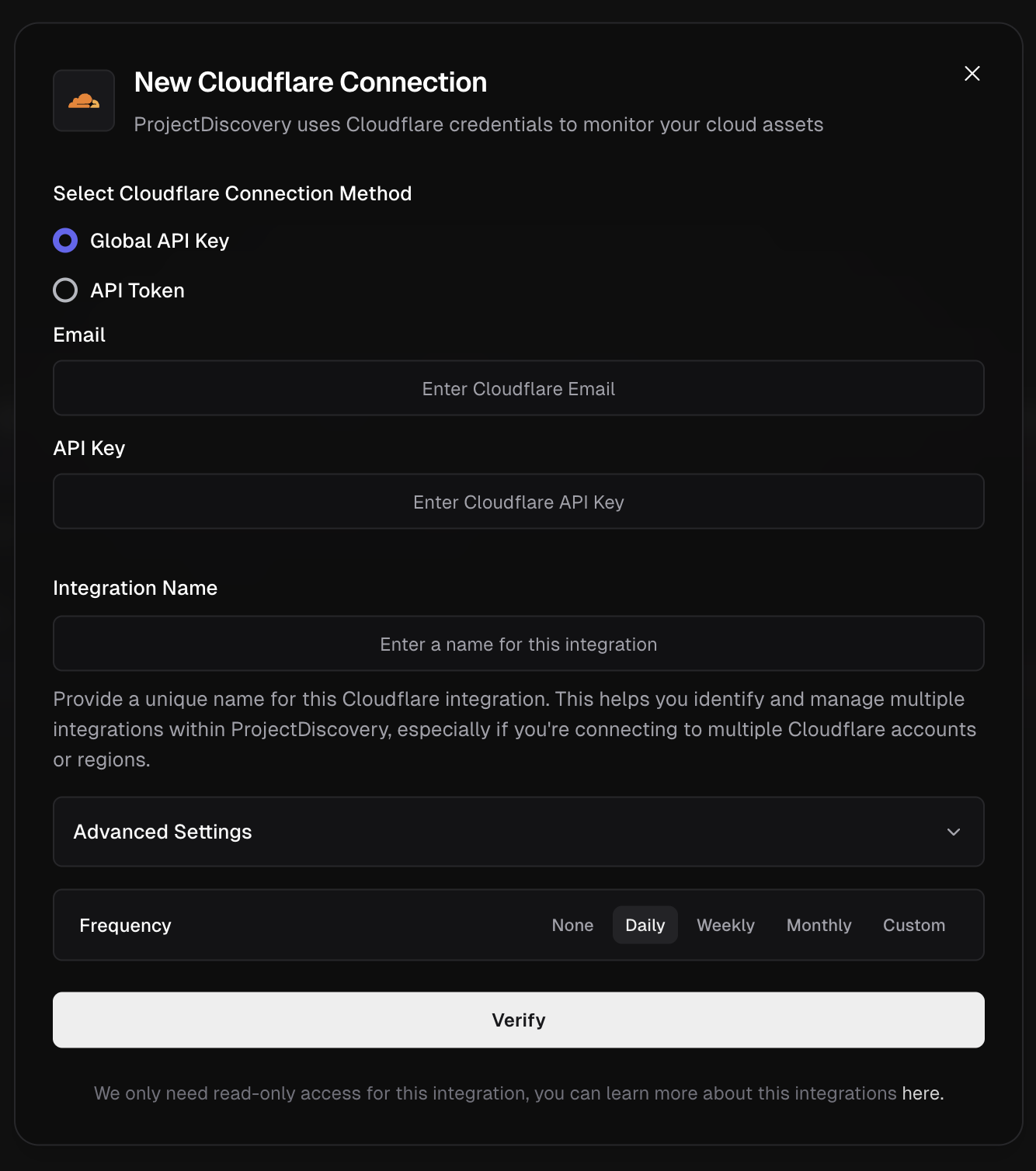
Cloudflare
Configure Cloudflare Integration
Click here to open the Cloudflare integration configuration page in the ProjectDiscovery Cloud platform
- DNS and CDN assets
- Global API Key
- Go to Cloudflare Dashboard.
- Under “API Keys”, locate the Global API Key and click View.
- Authenticate and copy the key.
- Now enter the Cloudflare account email and Global API Key copied in above step into ProjectDiscovery Cloud Platform.
- Give a unique Integration name and click Verify.
- API Token (Recommended)
- From the Cloudflare dashboard ↗, go to My Profile > API Tokens.
- Select Create Token > choose Create Custom Token.
-
Set the following read-only permissions required for asset discovery:
Permission Group Permission Access Zone Zone Read Zone DNS Read - Under Zone Resources, select All zones (or choose specific zones to limit scope).
- Click Continue to summary > Create Token and copy the generated token.
- Now enter the API Token in ProjectDiscovery Cloud Platform.
- Give a unique Integration name and click Verify.
- https://developers.cloudflare.com/fundamentals/api/get-started/create-token/
- https://developers.cloudflare.com/fundamentals/api/reference/permissions/
Fastly
Configure Fastly Integration
Click here to open the Fastly integration configuration page in the ProjectDiscovery Cloud platform
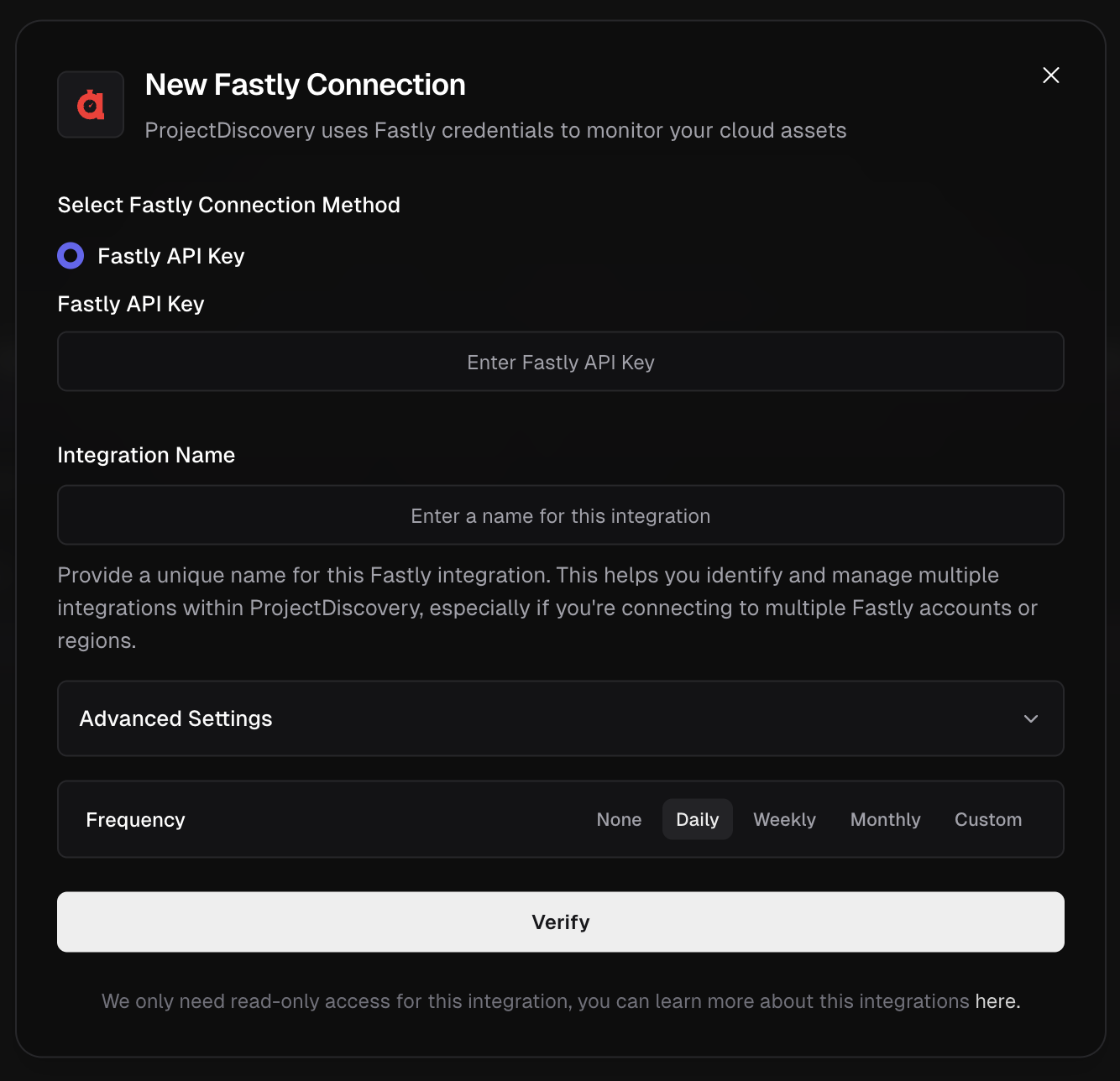
- Go to Fastly account settings.
- Under API, click Create API token if you don’t already have one.
- Copy the API Key.
- Now enter API Key in ProjectDiscovery Cloud Platform.
- Give a unique Integration name and click Verify.
DigitalOcean
Configure DigitalOcean Integration
Click here to open the DigitalOcean integration configuration page in the ProjectDiscovery Cloud platform
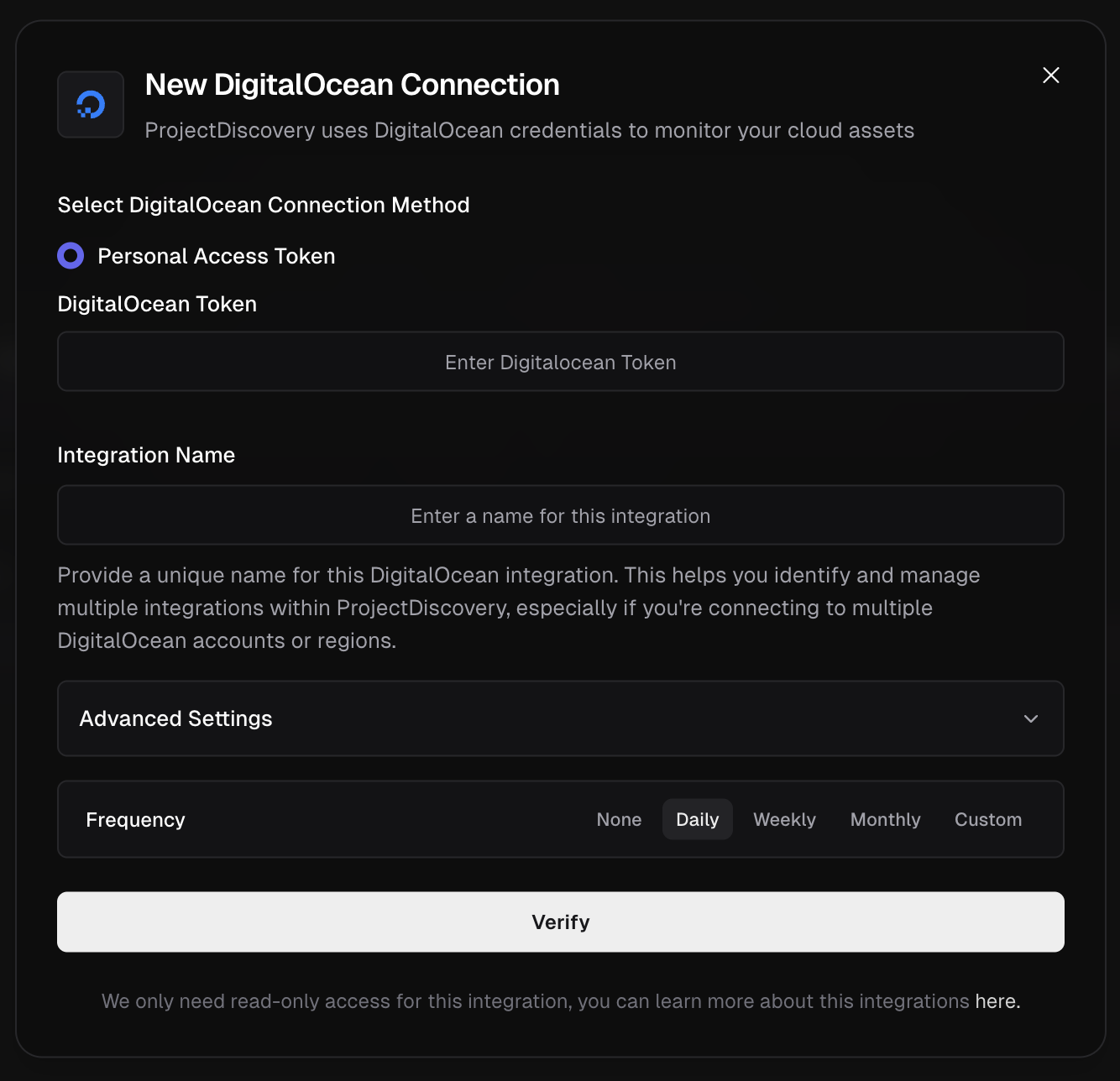
- Go to DigitalOcean API Settings.
- Click Generate New Token
- Provide a name and enable read-only access scope
- Copy the token
- Now enter token in ProjectDiscovery Cloud Platform.
- Give a unique Integration name and click Verify.
- Droplets and managed services