Summary
Every organization is unique in their tech stack composition. You need to detect and remediate a whole range of vulnerabilities that are not just limited to publicly known attacks. Our Cloud platform can automate scanning for almost any kind of vulnerability, including those you know about internally, across your environments. Review this use case to walk through an example to create a template for custom automation.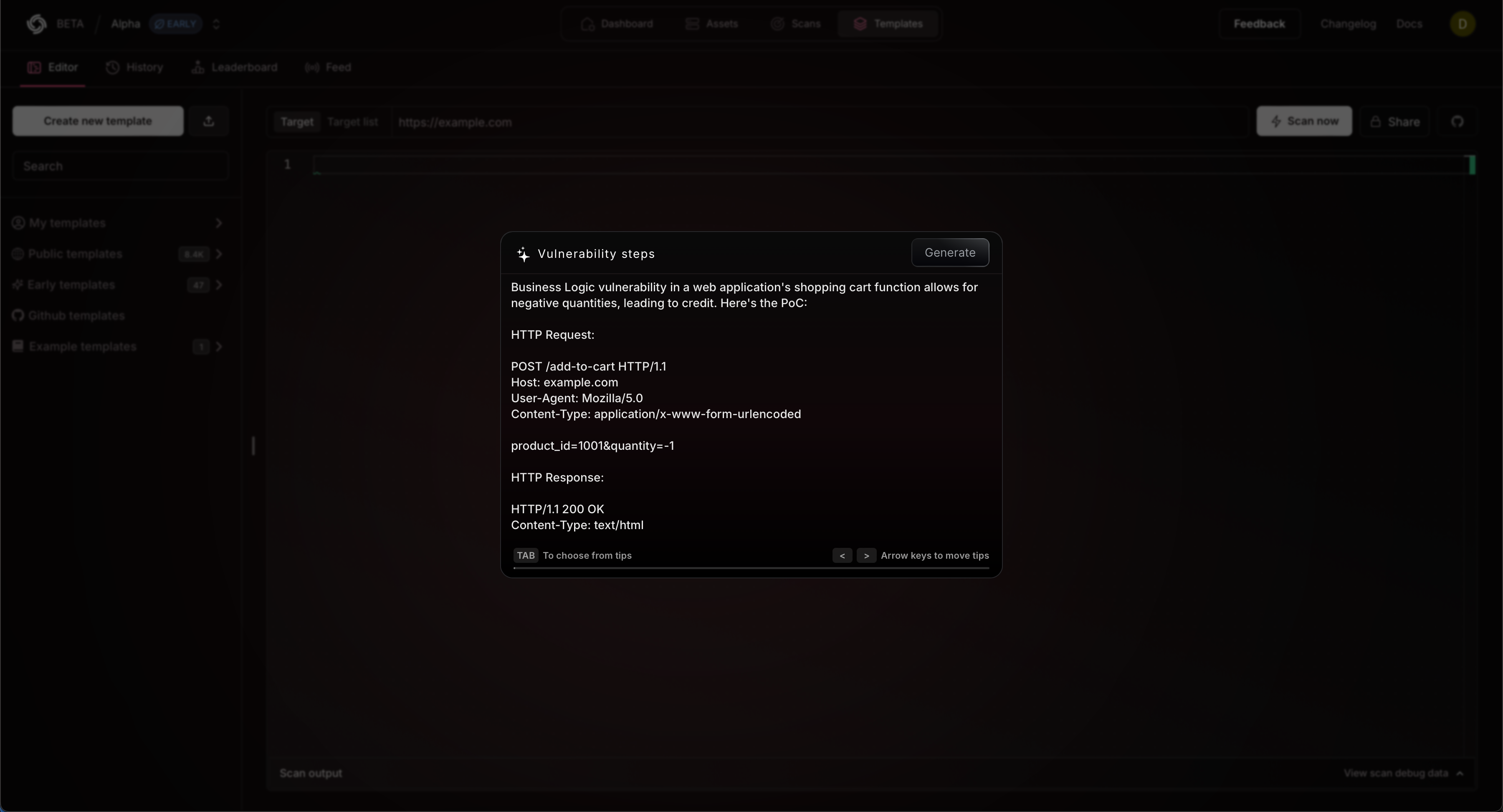
Custom automation
Imagine your penetration testing team found a critical vulnerability onapp.hooli.com. Now, you want to inspect to look for this vulnerability on your other instances or ensure it does not reappear in the future on the same app:
Example
Create a Custom Template
Follow the steps below to build a custom template and automation.1
Open Templates
Navigate to https://cloud.projectdiscovery.io/templates and select Start with AI to open the workflow.
2
Add your template
Paste your template and click Generate to build a new custom template.
- This will take a moment to create a new template.
- Use the example above to test this functionality out.
3
Revise your template
Our template language is easy and versatile, allowing you to write nearly any type of vulnerability test.
- To make additional edits check out our templates doc to learn more.
4
Build a new Scan
Navigate to https://cloud.projectdiscovery.io/scans and select Create New Scan to open the workflow to create a new scan using the template
you just created.
What’s Next?
This workflow can quickly turn your internal vulnerability knowledge into continuous scans. Monitor across your tech stack to see its match and re-appearance after the fix. This approach helps identify similar matches and reappearances after implementing fixes. Through these customizations you can easily build a security monitoring system that expands upon the expertise and data of your security teams.- Review scanning basics
- Explore continuous scanning
- Check for a trending vulnerability