Agent based Scanning
Use pd-agent for seamless internal scanning through our platform. Perfect for large networks and centralized security management.
Local Scanning & Upload
Run Nuclei locally and upload results to PD’s platform. Ideal for teams with existing scanning workflows or specific network restrictions.
Internal scanning helps identify misconfigurations, unpatched systems, and security gaps that could be exploited for lateral movement before attackers can leverage them.
Method 1: Agent based Scanning (Recommended)
To use this feature you’ll need to install and deploy pd-agent within your internal network. The agent acts as a bridge between your internal infrastructure and ProjectDiscovery’s platform, enabling you to trigger and manage scans remotely.What is pd-agent?
pd-agent is a lightweight agent that you deploy within your internal network to execute scans and enumerations remotely. It establishes a secure connection between your internal infrastructure and ProjectDiscovery’s platform, receives scan configurations and executes them locally using ProjectDiscovery’s tools. Key Capabilities:- Network Discovery: Automatically discover assets, services, and open ports across your internal network
- Vulnerability Scanning: Execute Nuclei-based vulnerability scans using templates from the ProjectDiscovery’s platform
- Agent Tagging: Organize agents with tags and networks for targeted execution
- Passive Discovery: Optional passive network discovery via libpcap/gopacket
- Automatic Updates: Receive and execute new scan configurations automatically
Agent based internal scanning is an Enterprise-exclusive feature. Free users can still perform internal scans using the local scanning method described below.
System Requirements
The agent is designed to be lightweight and efficient. Minimum recommended specifications for optimal performance:
The agent is designed to be lightweight and efficient. Minimum recommended specifications for optimal performance:
- CPU: 2 vCPU
- Memory: 4GB RAM
- Network: 100Mbps network interface
- Storage: 10GB available disk space
- Operating System: Linux (recommended), macOS, or Windows
Step 1: Create a Network
Before installing the agent, you need to create a network in the ProjectDiscovery’s platform. Each network represents a distinct internal environment (e.g., production, staging, office network) and generates a unique agent configuration.- Navigate to https://cloud.projectdiscovery.io/networks
- Click “Create Network”
- Provide a network name
- Save the network to generate your unique agent installation command
You can create multiple networks for different environments or network segments. Each network can have one or more agents deployed.
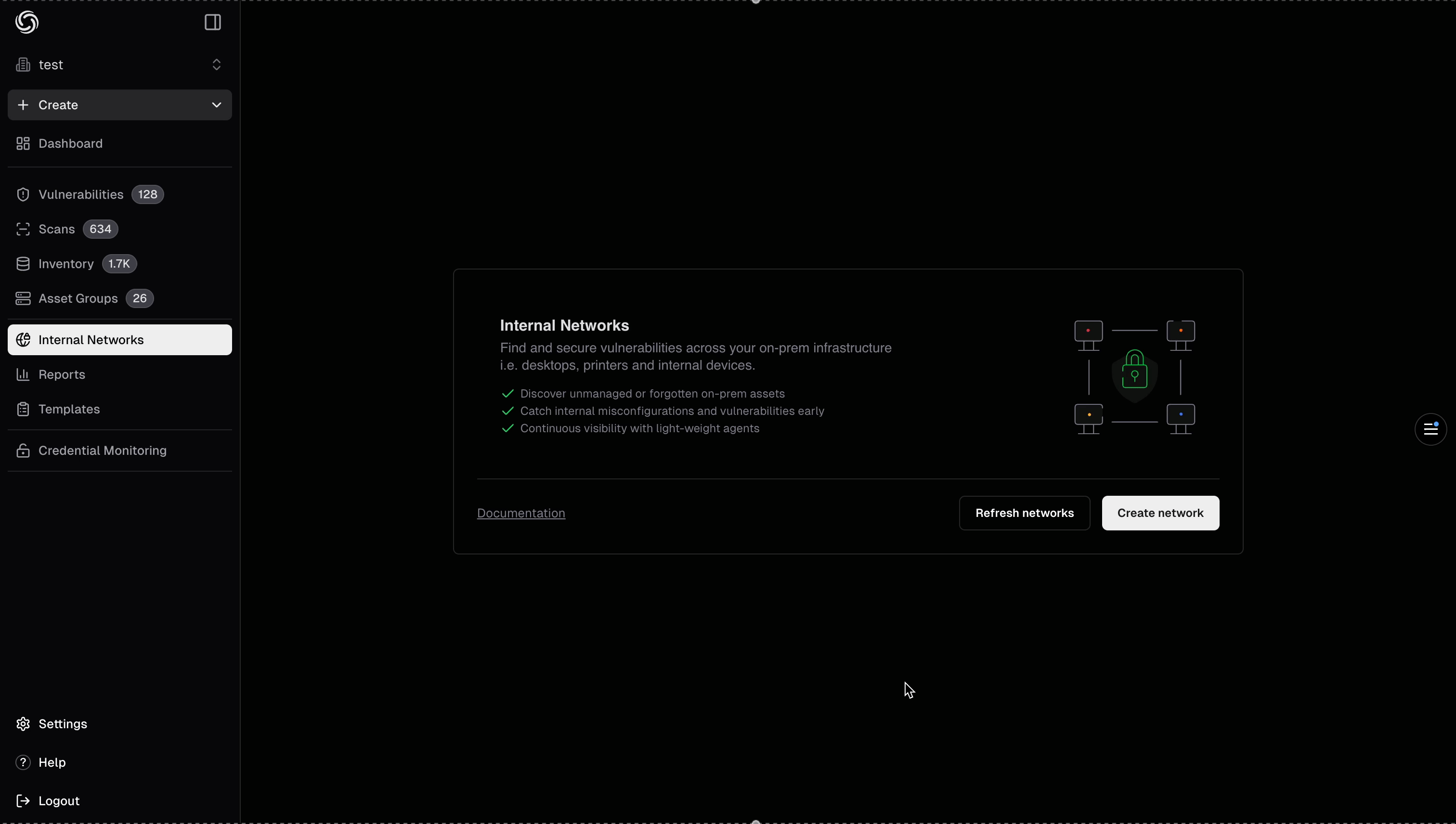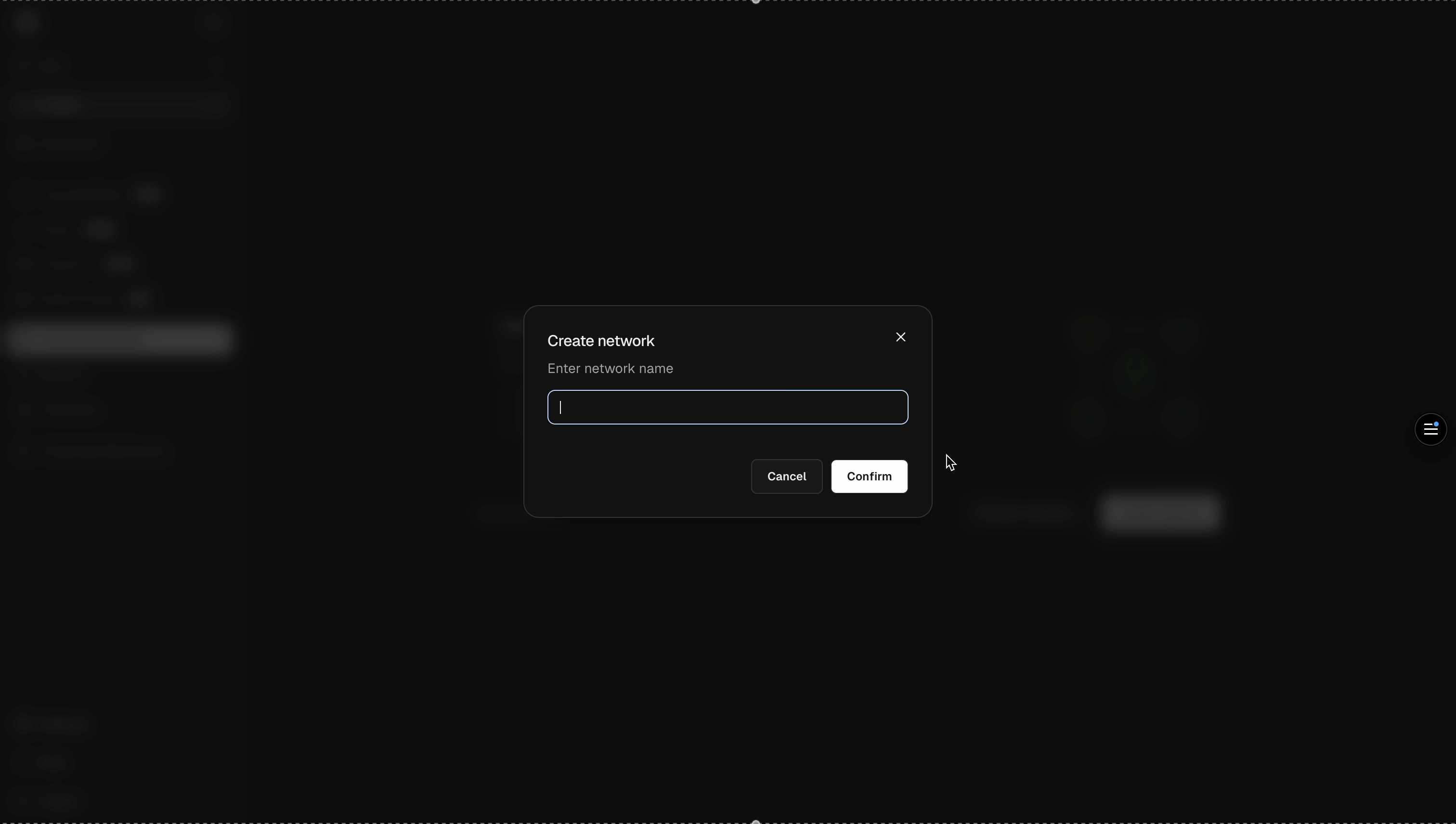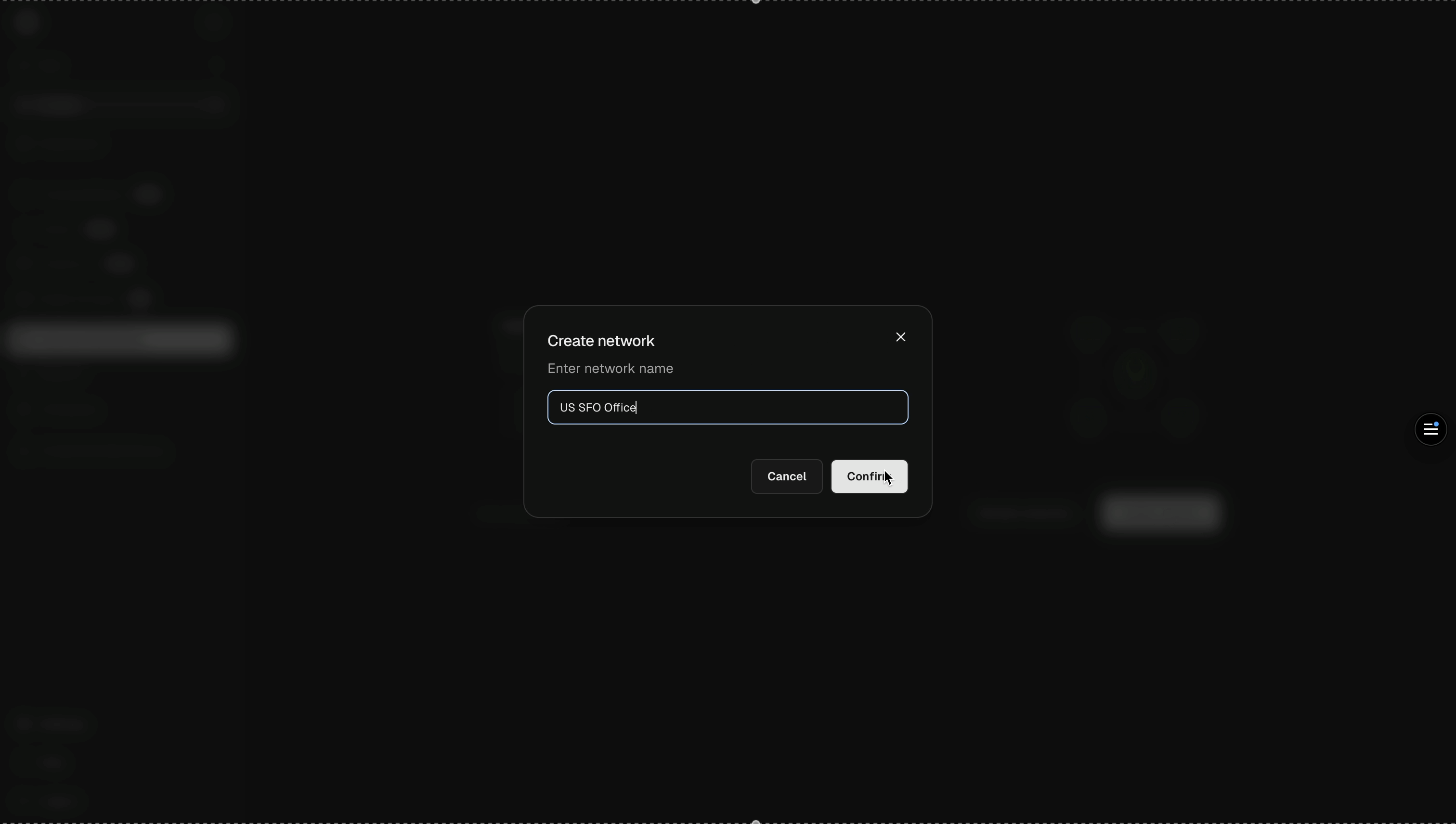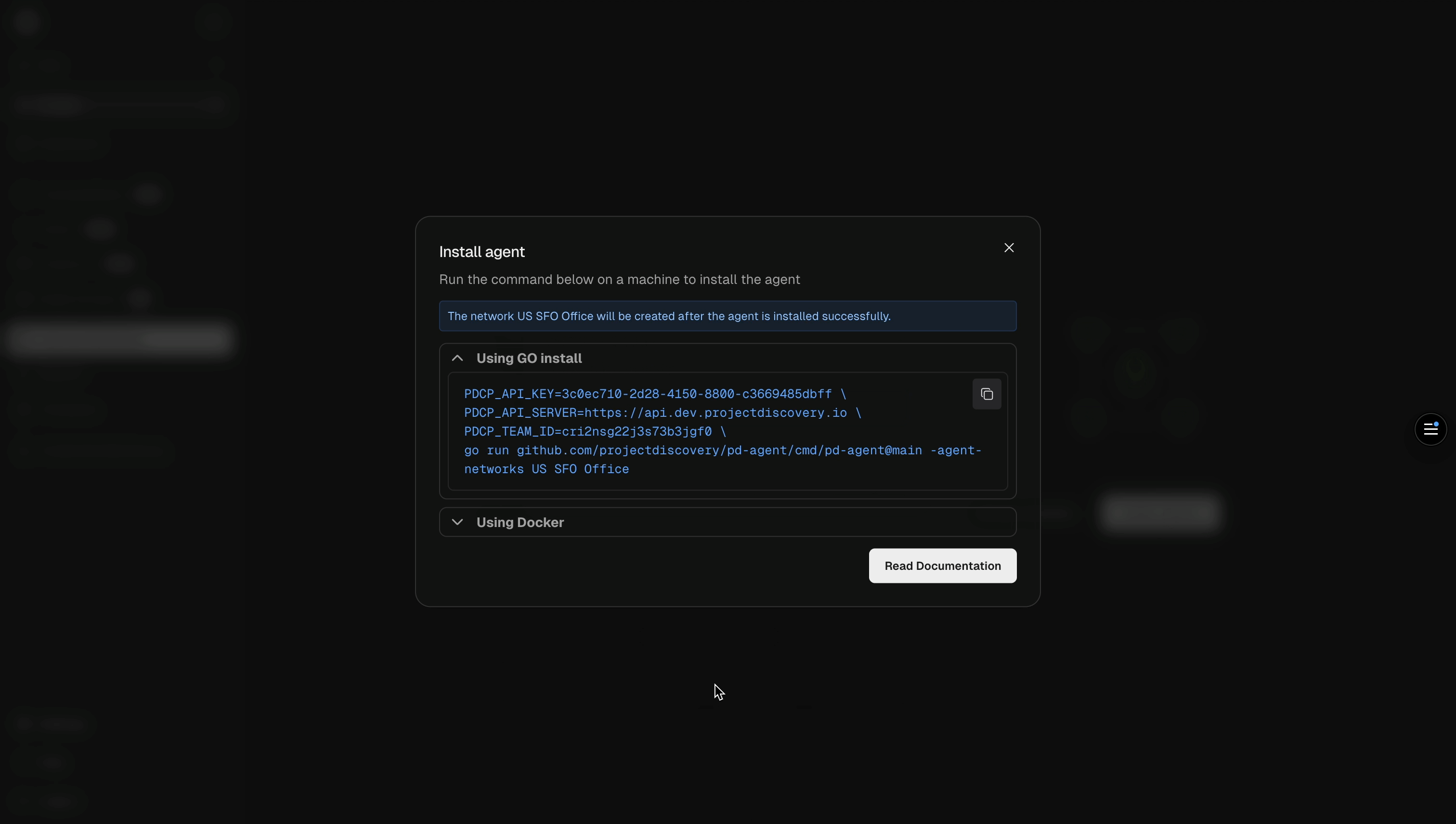
Step 2: Install the agent
After creating your network, the platform will display a unique installation command pre-configured with your credentials and network settings.Prerequisites for Go installation methodIf you’re using the Go command option to install pd-agent, ensure you have:Or combine both commands:
- Go installed on your system (download Go)
- pdtm (ProjectDiscovery Tool Manager) installed
- Download and configure the agent
- Establish a secure connection to ProjectDiscovery’s platform
- Register the agent with your network
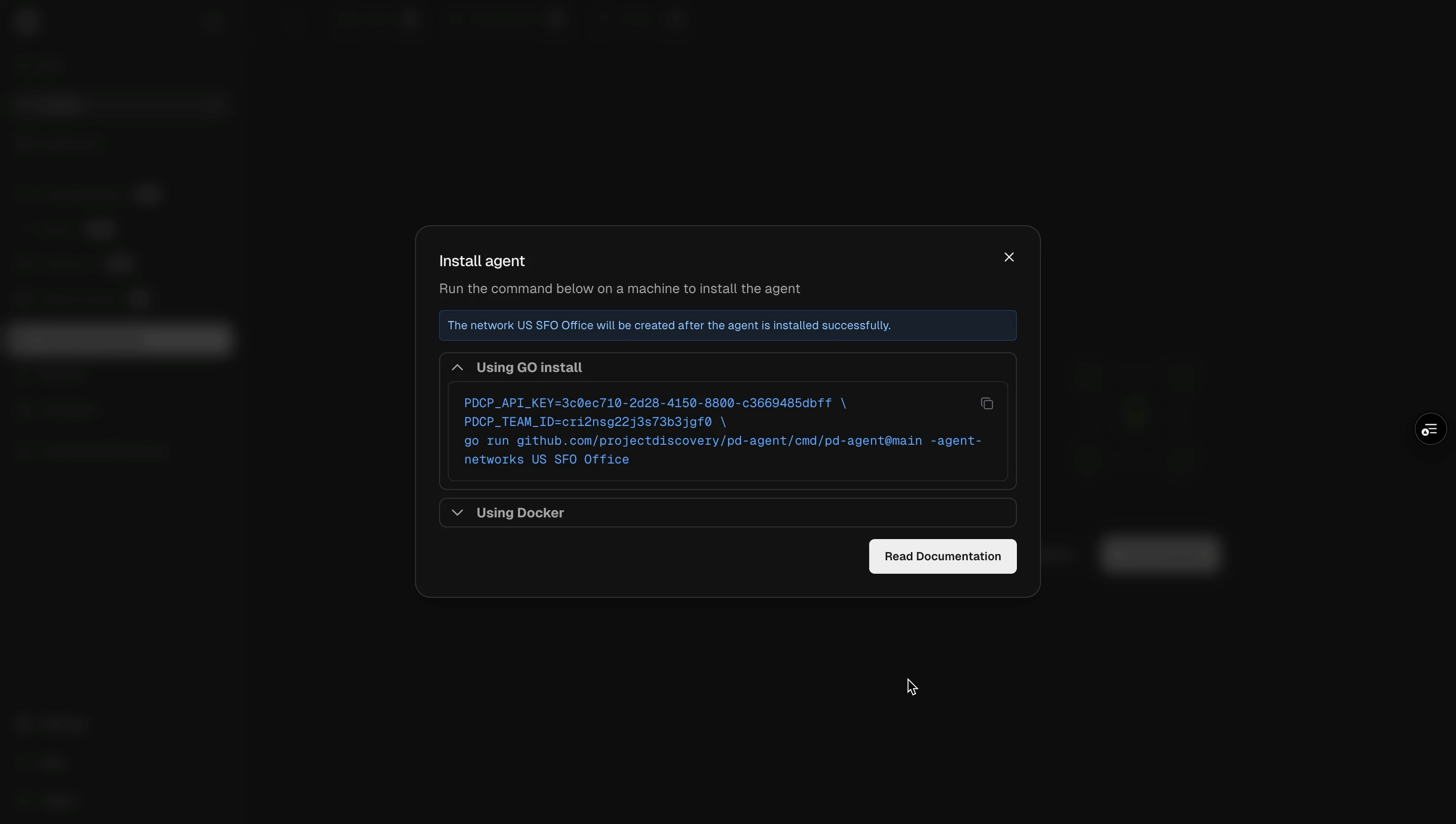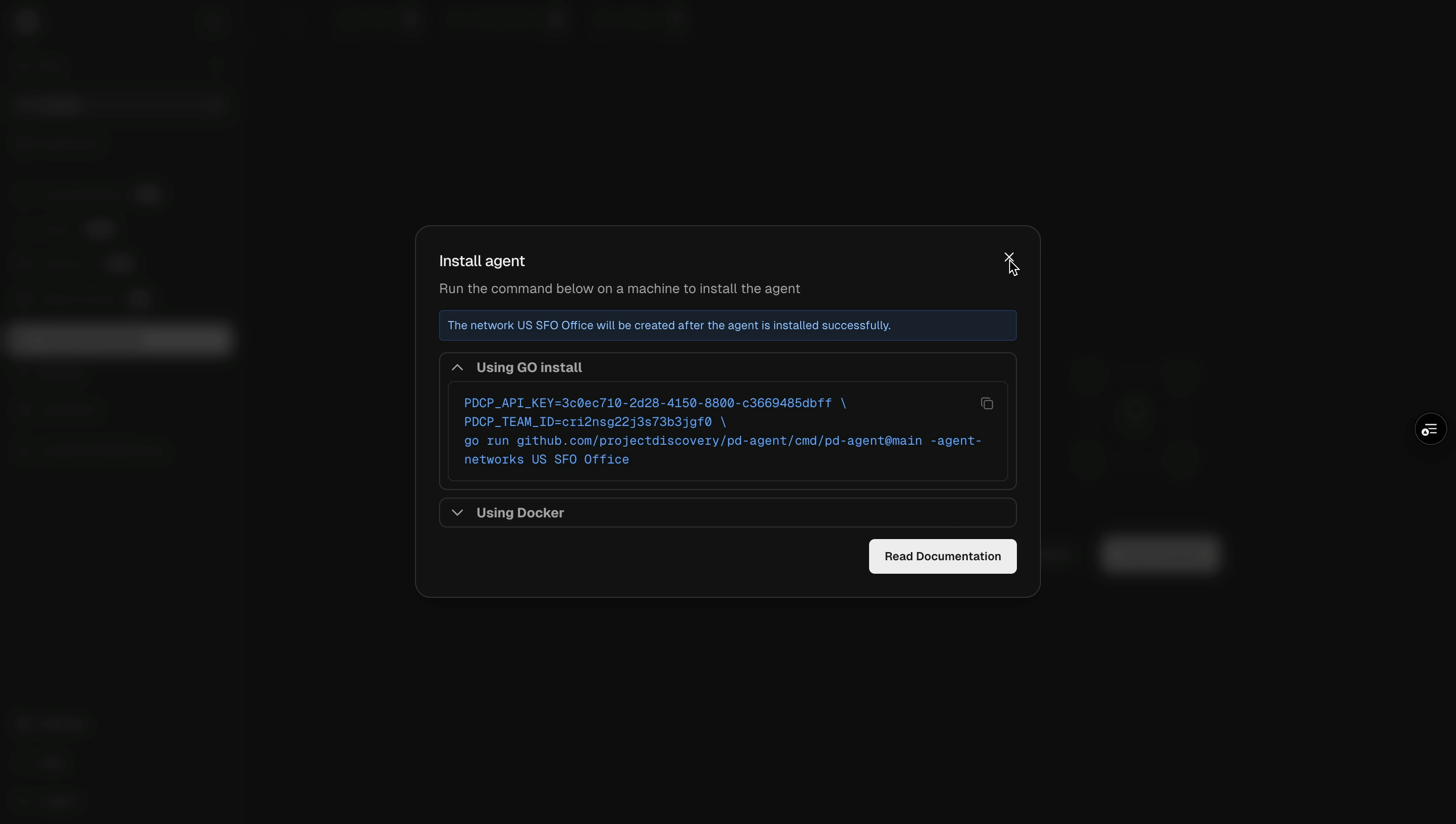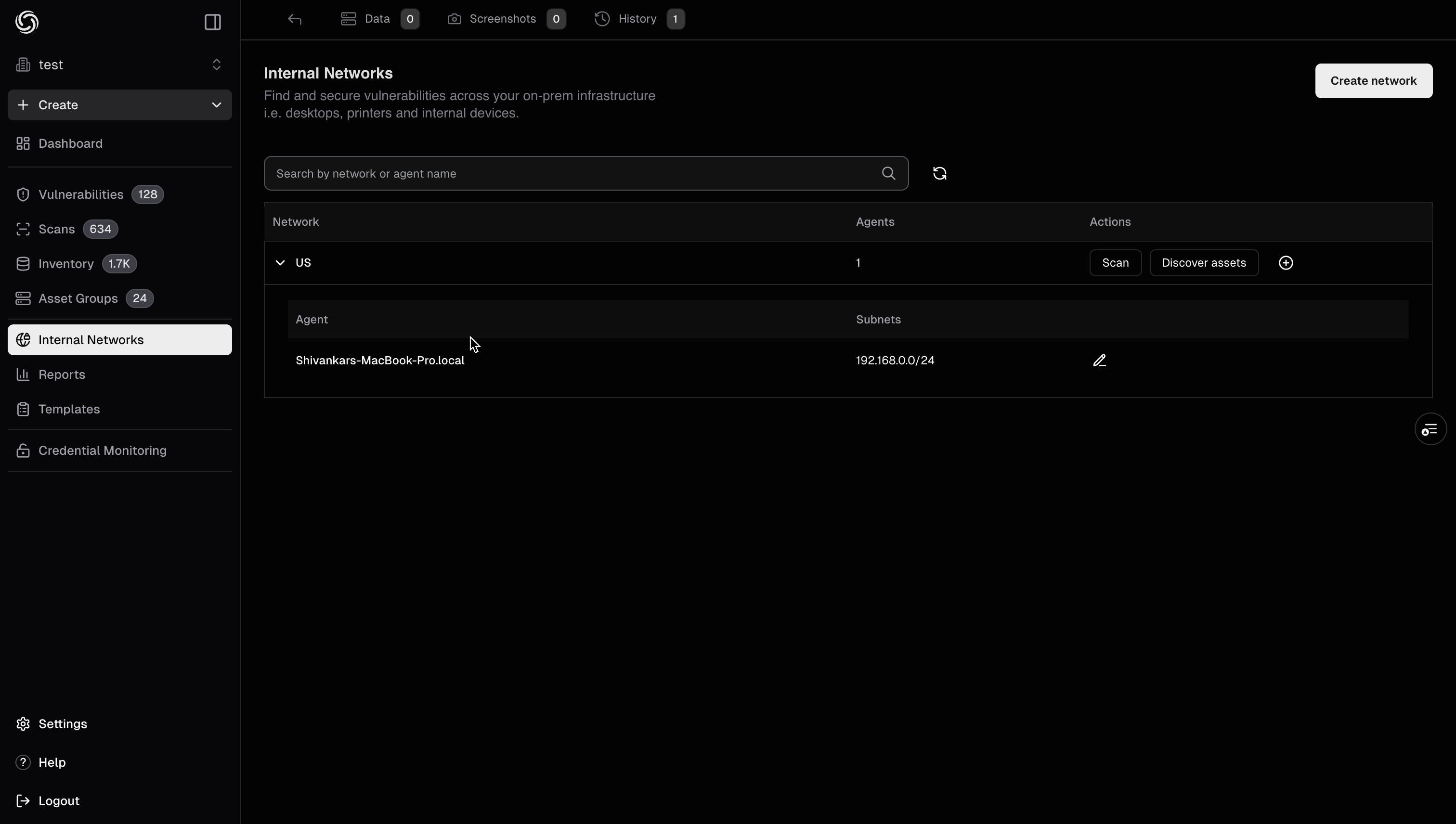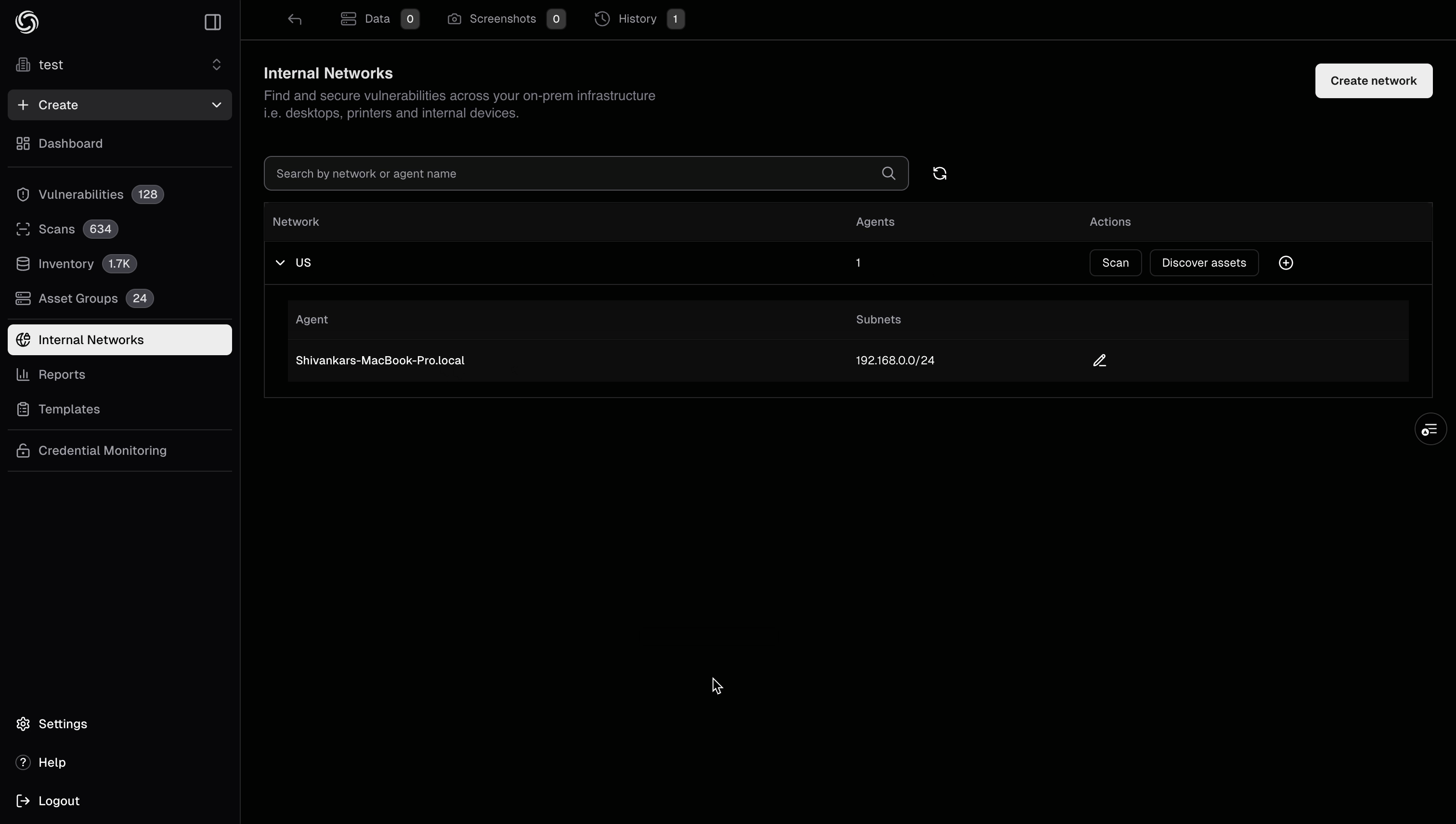
The agent must remain running to execute scans. For production deployments, consider running it as a system service (systemd, Docker, or Kubernetes) to ensure it stays active.
Step 3: Discover Assets
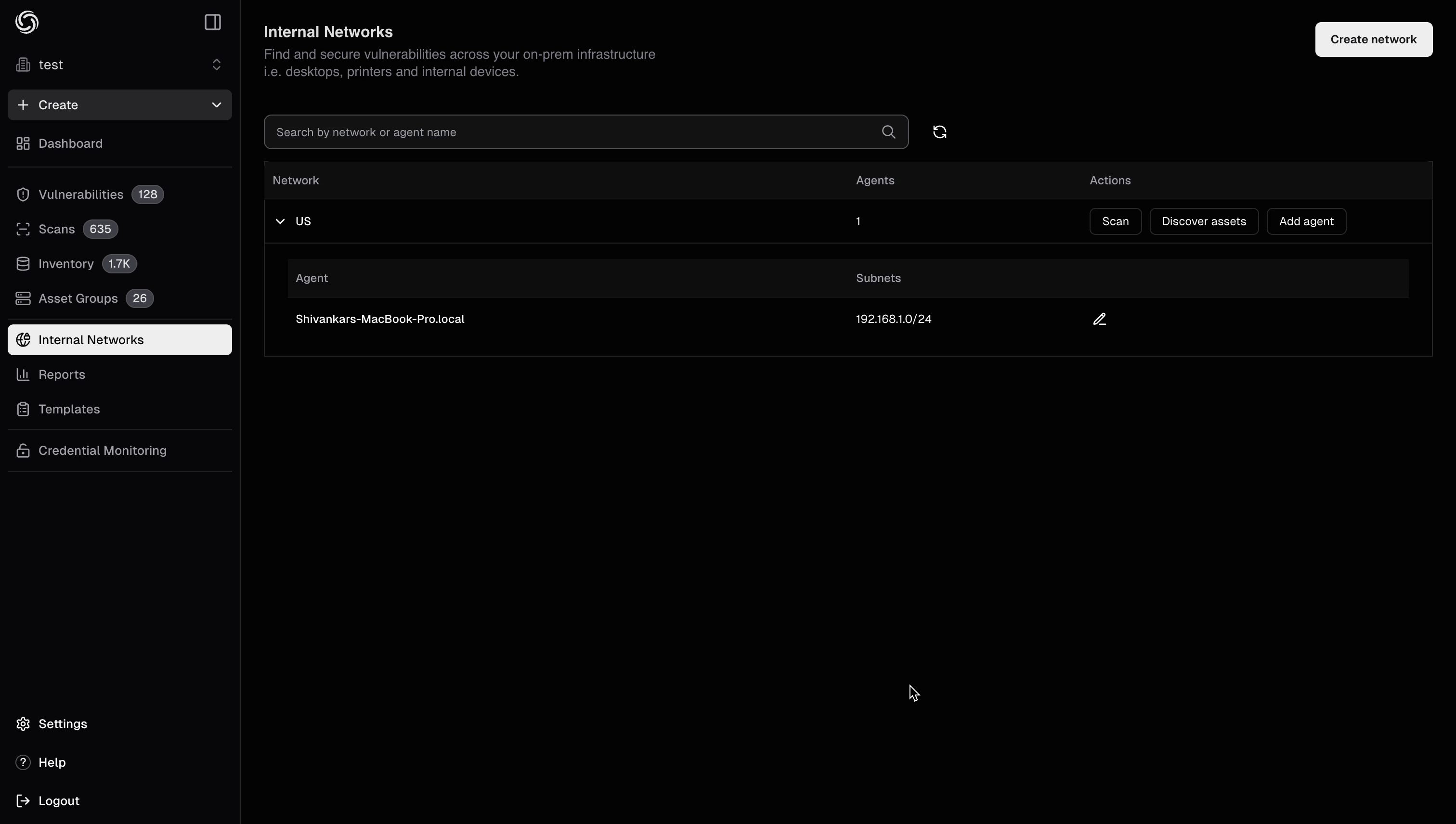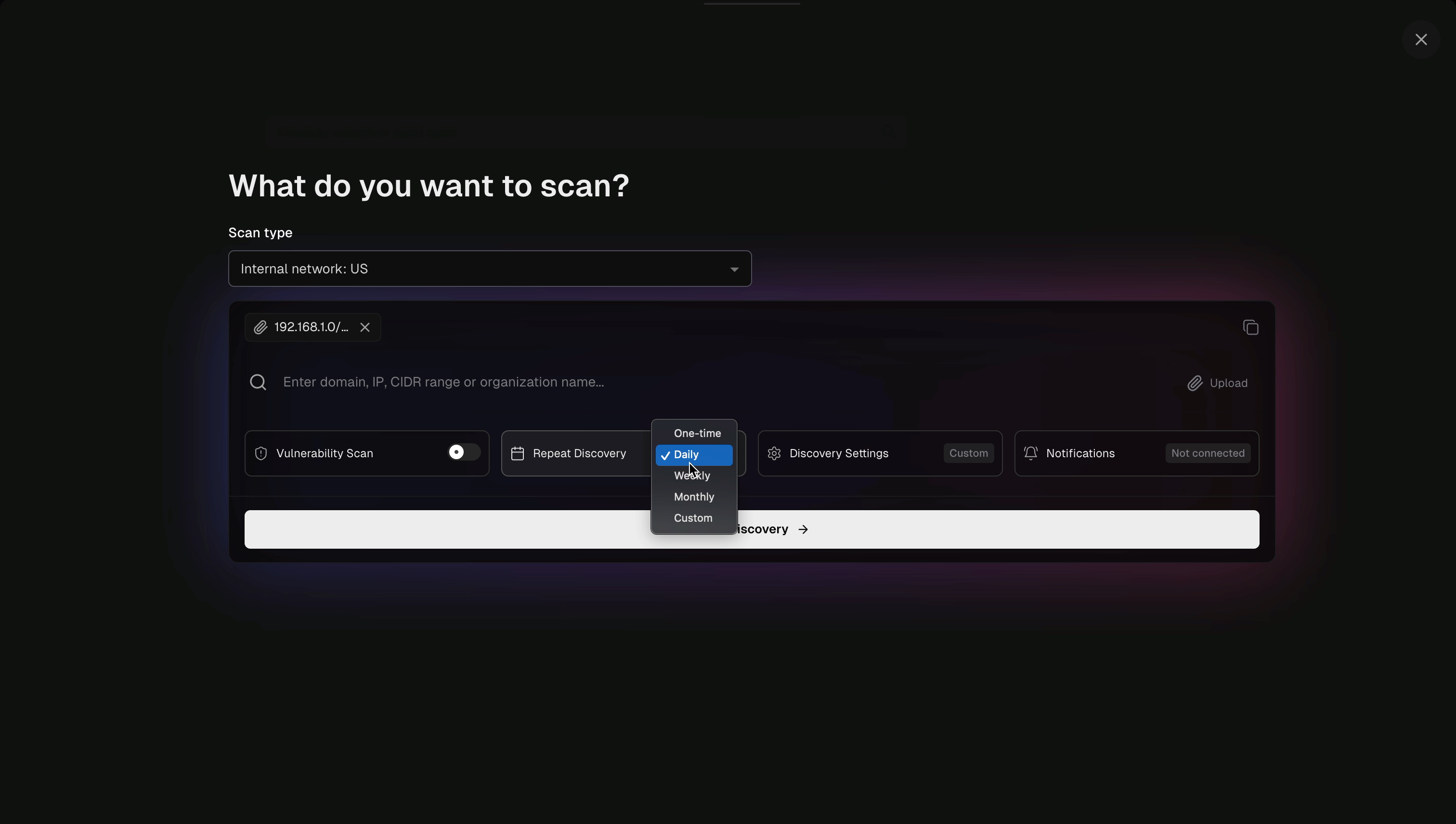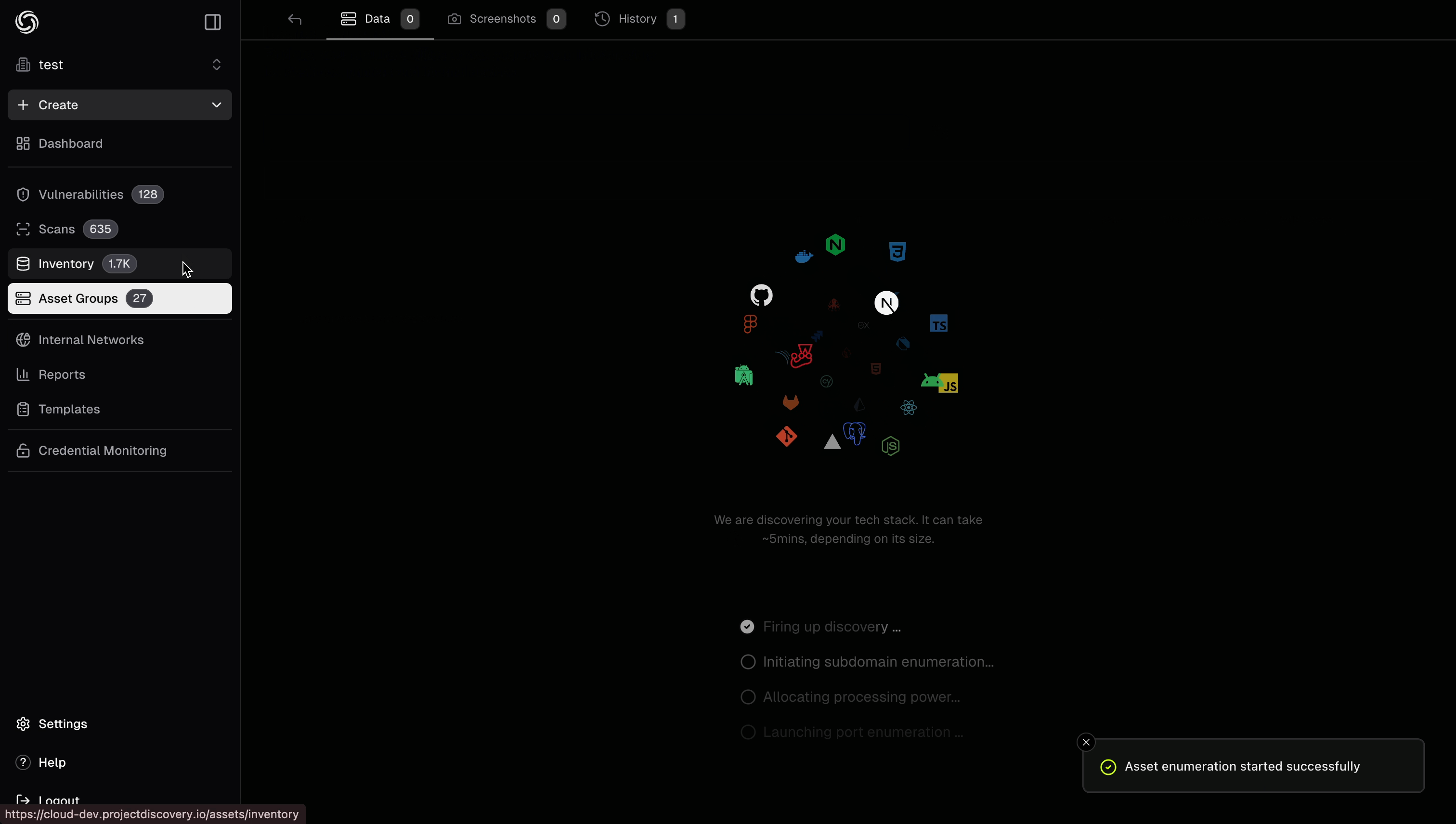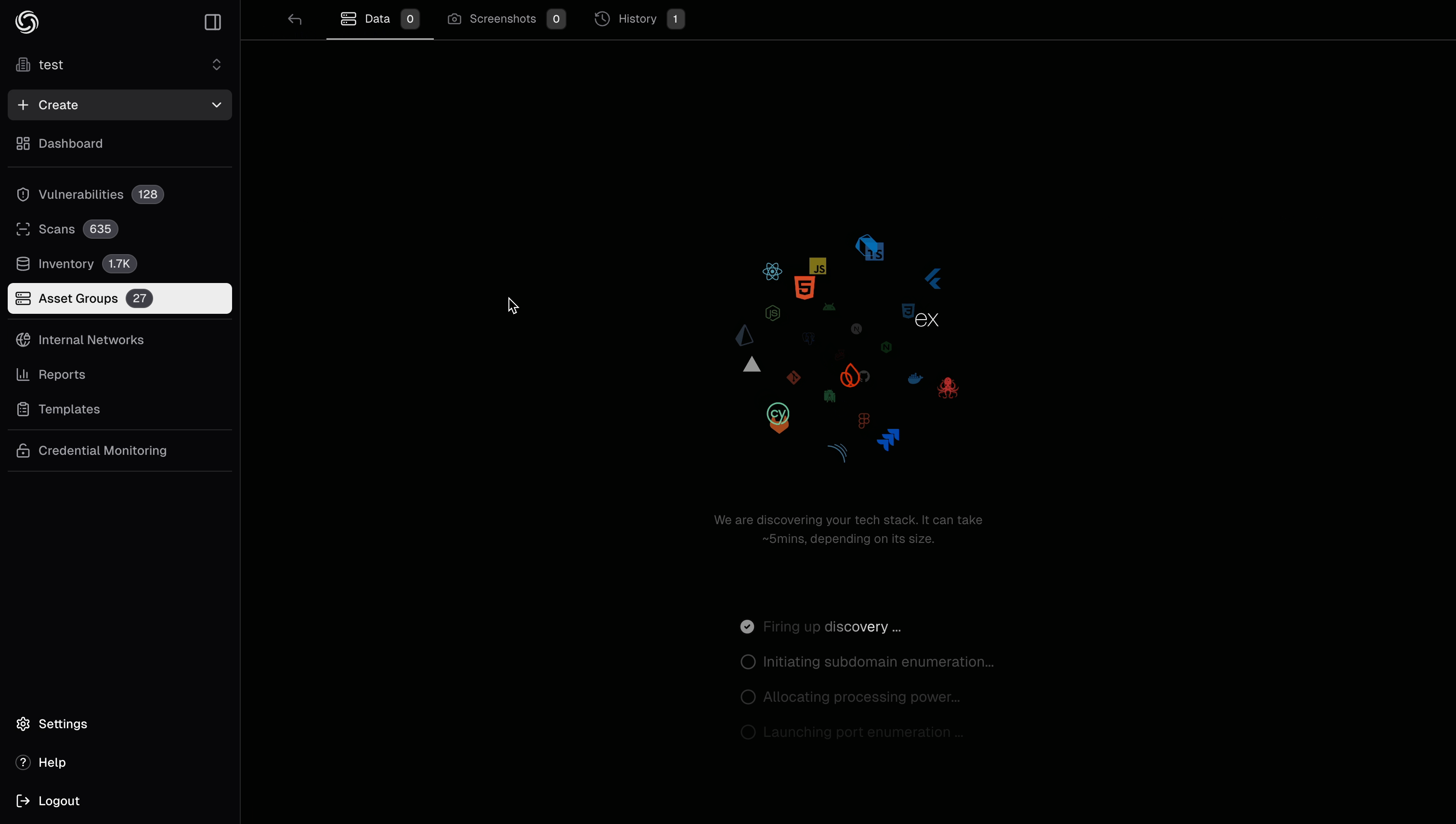
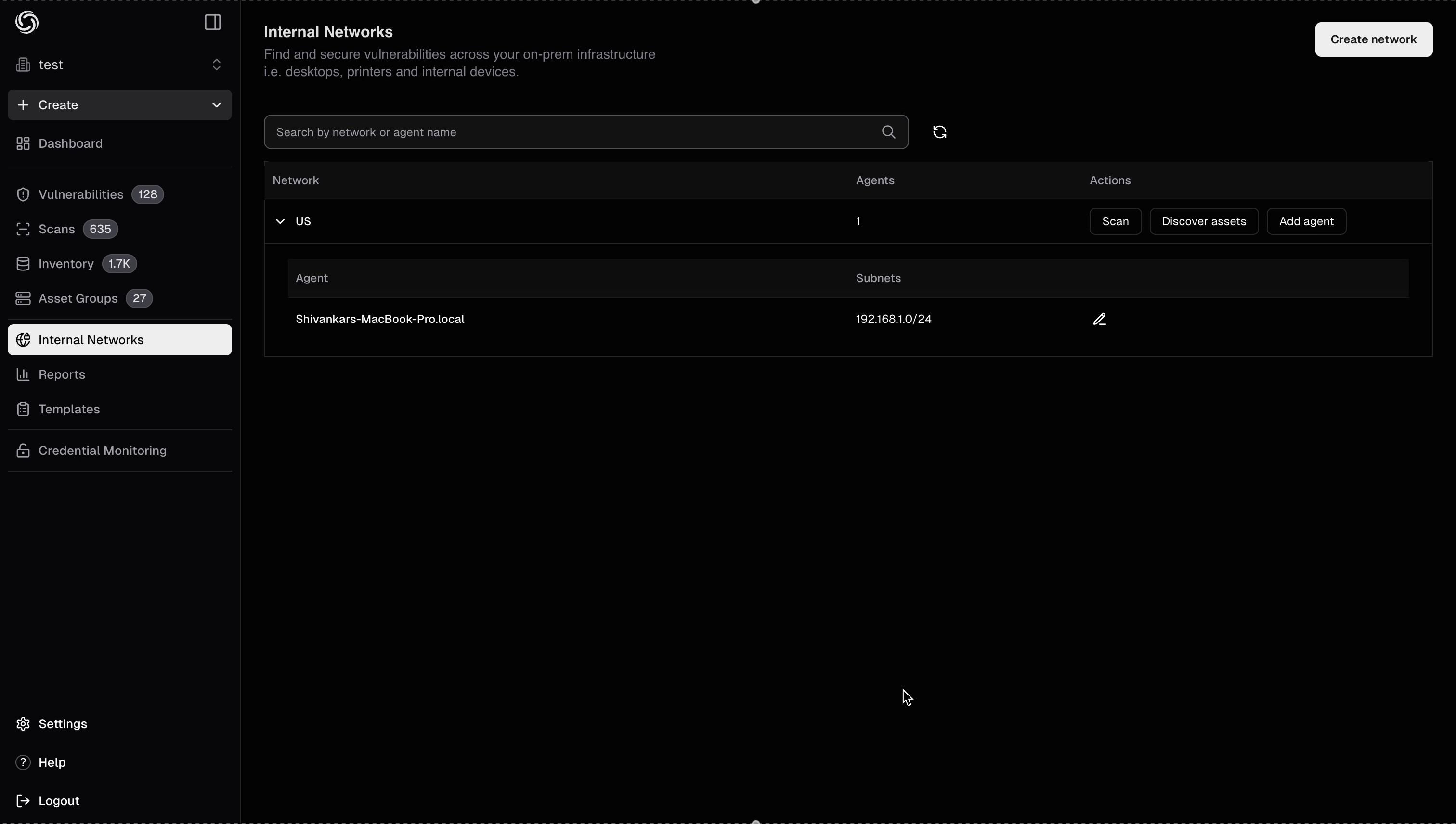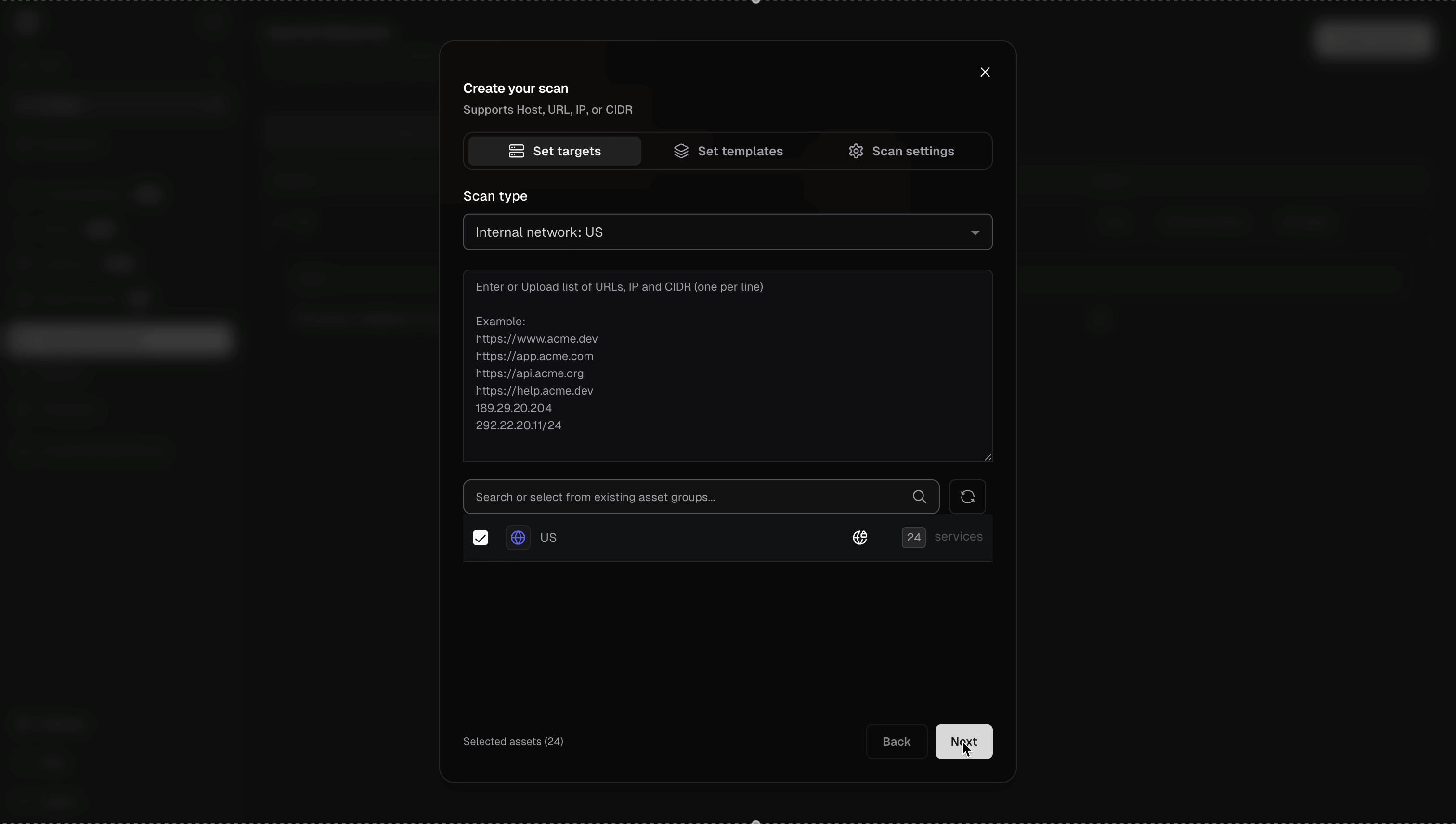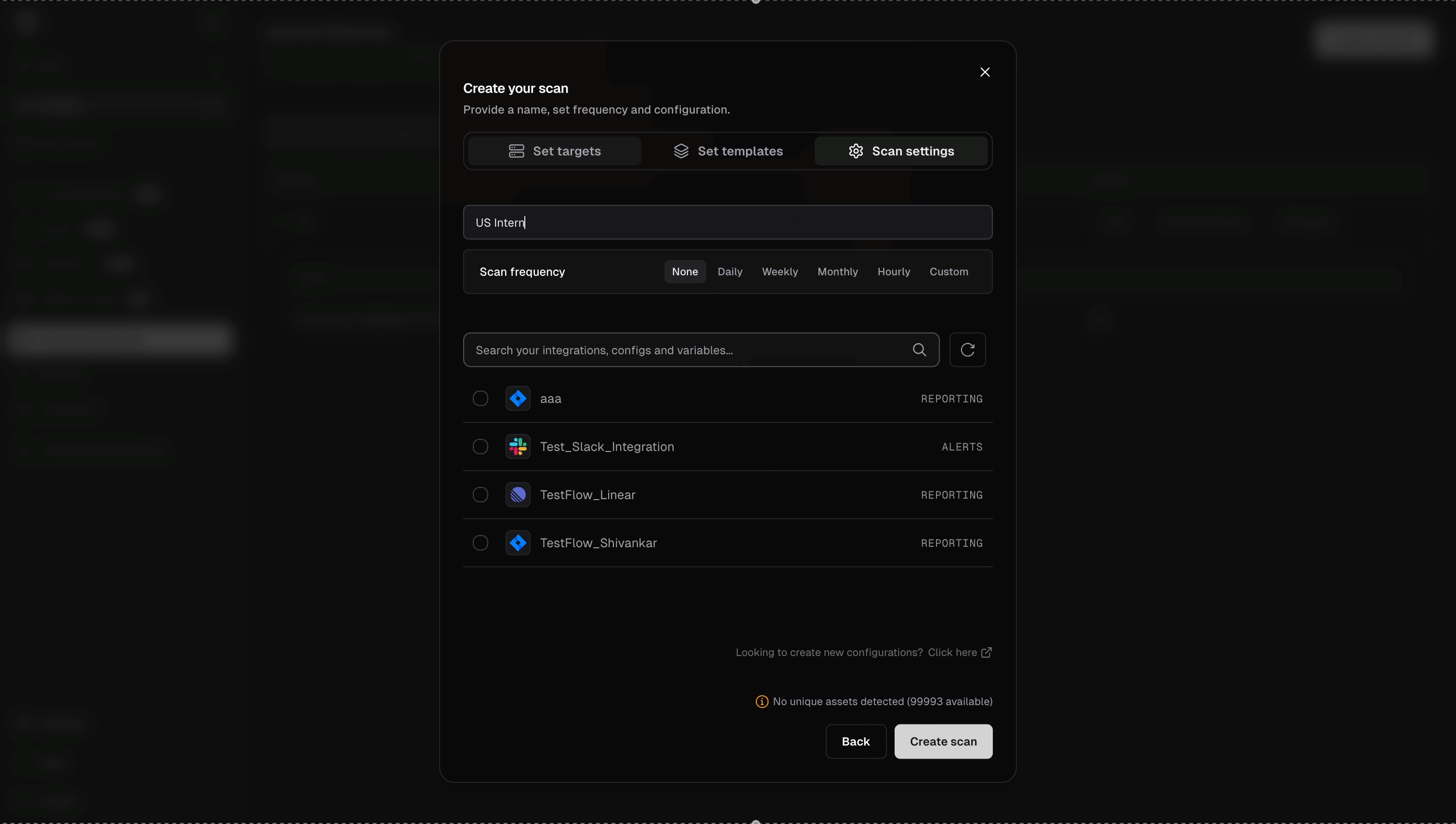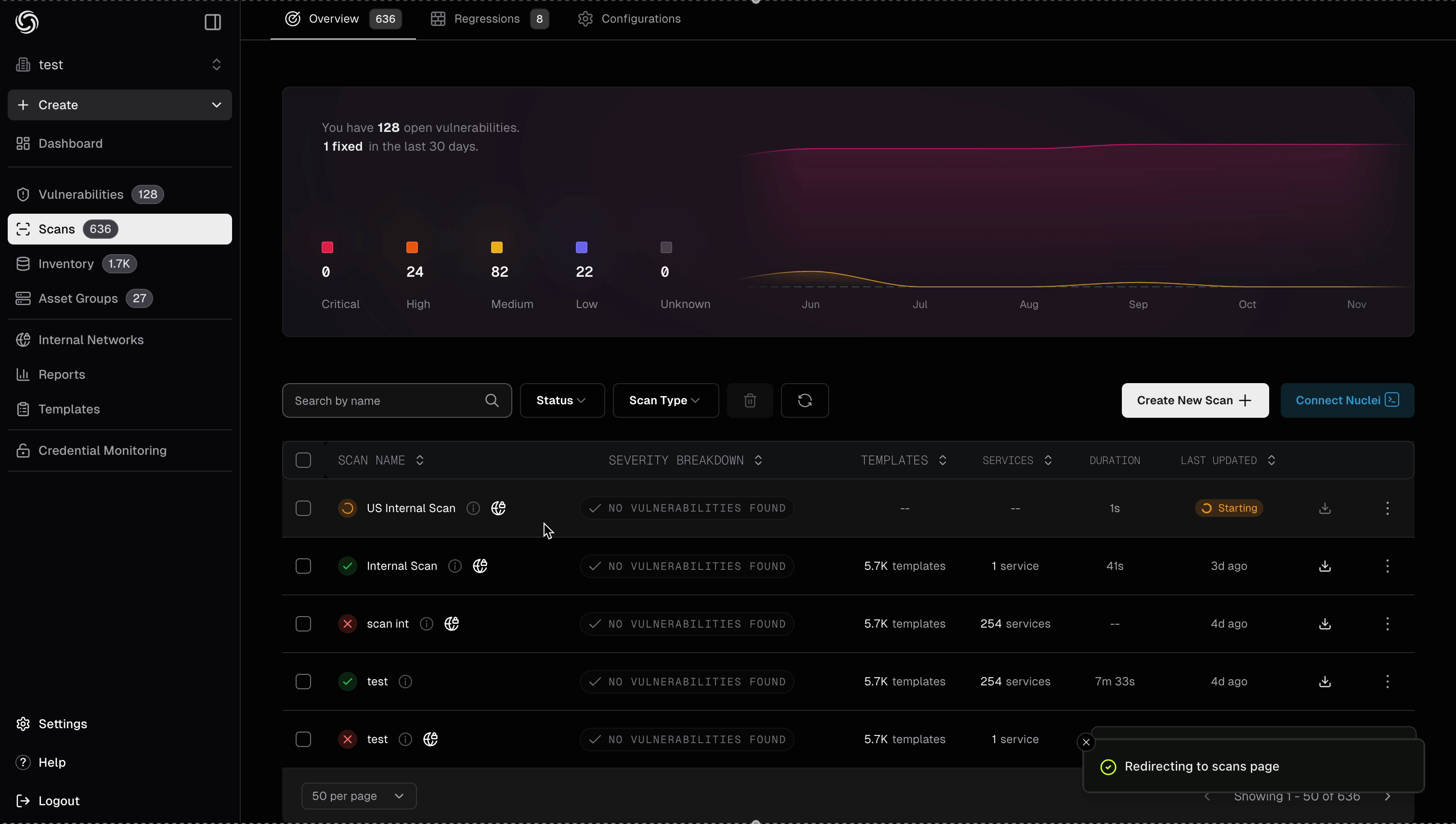
Before running vulnerability scans, you can discover assets in your internal network. This helps you identify all hosts, services, and open ports that the agent can reach.- Navigate to your networks dashboard at https://cloud.projectdiscovery.io/internal-network
- Locate the network you want to discover assets for and click the Discover assets button under the Action column
- Configure your discovery parameters (target ranges, ports, discovery methods, etc.)
- Click on Start Discovery to initiate the discovery process. The pd-agent will scan your internal network and discovered assets will appear in your asset inventory
Asset discovery helps you build an accurate inventory of your internal infrastructure before running targeted vulnerability scans. This ensures comprehensive coverage of your attack surface.
Step 4: Trigger Internal Scans
Once your pd-agent is connected and assets are discovered (optional), you can trigger vulnerability scans. The workflow is identical to external scanning - configure scans through the same interface and view results in the same dashboard.- Click on the Scan button for the network you want to scan, or go to the Scans menu (https://cloud.projectdiscovery.io/scans) and click Create New Scan, choose Internal followed by the network
- Select the Asset Group created from the previous discovery operation, or manually enter your targets (internal IPs, hostnames, or CIDR ranges like
192.168.1.0/24,internal-server.local) - Select Nuclei templates (CVEs, misconfigurations, vulnerabilities, etc.) and configure scan settings (rate limits, headers, parameters)
- Click Create Scan to start - the scan executes through pd-agent in your internal network and results appear in your dashboard
Internal scanning provides the same experience as external scanning - identical template selection, scan configuration, results viewing, retesting capabilities, and integration options.
Important: Only input targets that are accessible from where pd-agent is deployed. If the agent is running on a server in your 192.168.1.0/24 network, it can only scan hosts within that network or other networks it has routing access to.
Method 2: Local Scanning & Upload
This approach lets you run Nuclei locally and upload results to ProjectDiscovery Cloud Platform (ProjectDiscovery).Set up your API Key
To connect your existing Nuclei results to PDCP you will need to create a free API Key:- Visit https://cloud.projectdiscovery.io
- Open the setting menu from the top right and select “API Key” to create your API Key
- Use the
nuclei -authcommand, and enter your API key when prompted.
Configure Team (Optional)
If you want to upload the scan results to a team workspace instead of your personal workspace, you can configure the Team ID using either method:-
Obtain Team ID:
- Navigate to https://cloud.projectdiscovery.io/settings/team
- Copy the Team ID from the top right section
-
CLI Option:
-
ENV Variable:
- Run your scan with the upload flag:
This method is ideal when you want to maintain complete control over scan execution or integrate with existing automation scripts.