Manual Retest
Manual retesting allows you to quickly verify the current status of specific vulnerabilities on-demand. This feature is designed for ad-hoc validation of findings, eliminating the need to run full scans repeatedly when you only need to check particular vulnerabilities.How Manual Retest Works
When you initiate a manual retest, you’ll be presented with a confirmation dialog: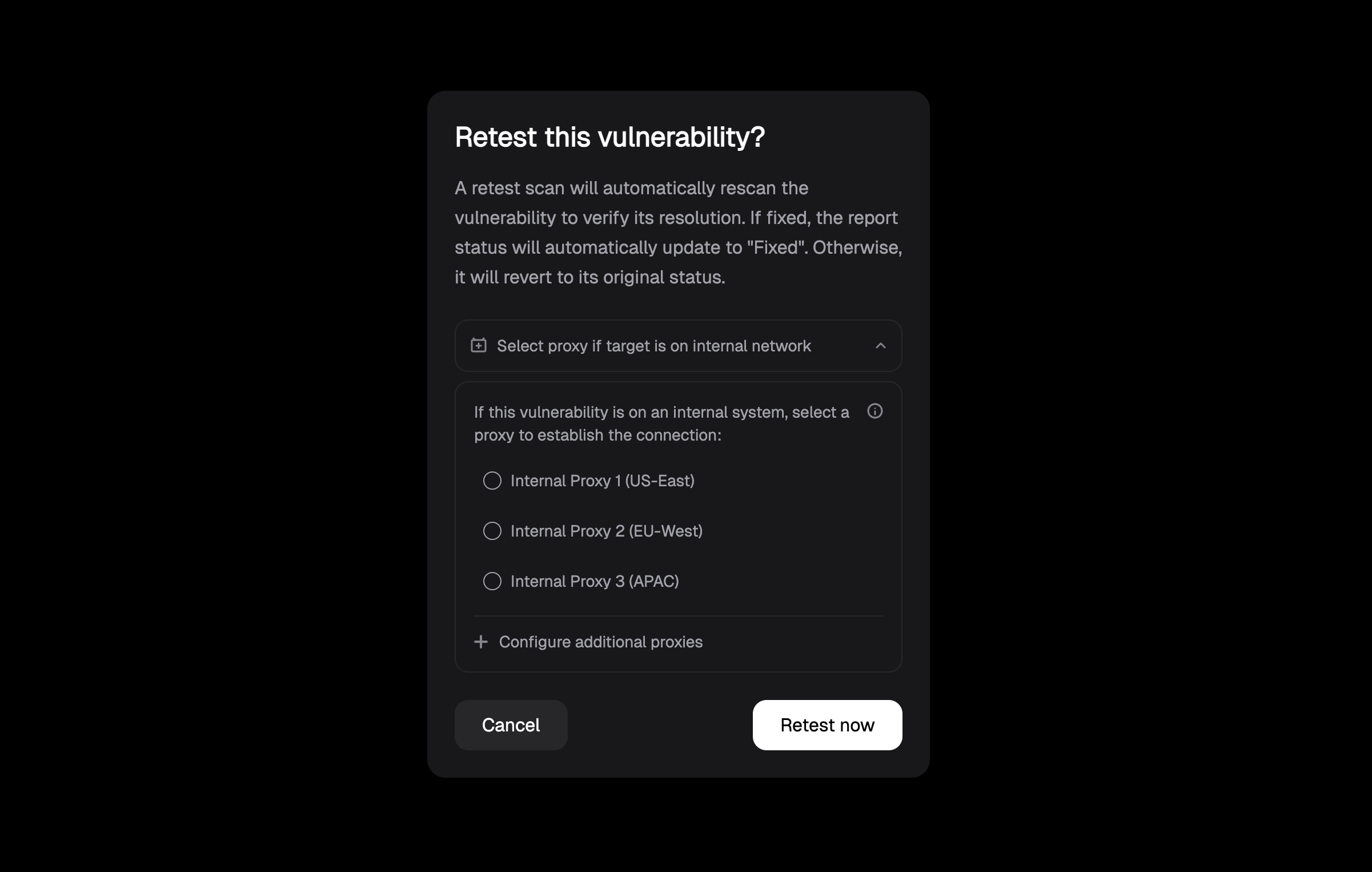
- Target specific vulnerabilities: Only tests the vulnerabilities you’ve selected
- Provide immediate results: Runs on-demand when you need verification
- Update status automatically: If the vulnerability is fixed, the status updates to “Fixed”; otherwise, it reverts to its original status
- Require minimal resources: Lightweight operation focused on specific findings
Auto Retest
The platform includes an automated retesting feature that runs daily to continuously monitor the status of your vulnerabilities. This feature is enabled by default and provides ongoing validation of your security posture without manual intervention.How Auto Retest Works
Auto retest automatically examines all open and fixed vulnerabilities in your system on a daily basis to:- Maintain accuracy: Ensures that vulnerability statuses reflect the current state of your assets
- Detect regressions: Identifies when previously fixed vulnerabilities have reappeared
- Provide visibility: Gives you clear insight into which vulnerabilities are actively exploitable
Manual Retest vs Auto Retest
The platform offers two distinct retesting approaches, each serving different needs:| Feature | Manual Retest | Auto Retest |
|---|---|---|
| Scope | Retests specific selected vulnerabilities | Retests all existing vulnerabilities in the system |
| Purpose | Ad-hoc validation of specific findings | Continuous validation and regression detection |
| Trigger | User-initiated, on-demand | Daily, automatic |
| Control | Full user control over what gets tested | Automatic, system-managed |
| Resource usage | Minimal, highly targeted | Lightweight, comprehensive coverage |
| Use case | Verify remediation of specific vulnerabilities | Maintain overall security posture |
| Timing | Immediate, when needed | Background, daily schedule |
When to Use Each Approach
Choose Manual Retest when:- You’ve just fixed a specific vulnerability and want immediate confirmation
- You need to validate remediation before a security review or audit
- You want to test a small subset of critical vulnerabilities quickly
- You’re working on specific issues and need real-time feedback
- Maintaining continuous security posture monitoring
- Detecting regressions without manual effort
- Keeping vulnerability statuses accurate across your entire portfolio
- Background monitoring that doesn’t require user intervention
Auto Retest vs Rescan: Auto retest only validates existing vulnerabilities in your system to check their current status, while rescanning performs comprehensive discovery to find new vulnerabilities. Auto retest is lightweight and focused on monitoring known issues, whereas rescans are resource-intensive and designed for complete security assessments.
Configuration
Auto retest is enabled by default. If needed, you can disable this feature by visiting your Auto Retest Settings.Supported Scenarios
External Vulnerabilities
- Direct retesting of vulnerabilities on externally accessible assets
- No additional configuration required
- Immediate validation of remediation status
Internal Vulnerabilities
The platform supports retesting of internal vulnerabilities in two scenarios:-
Cloud Platform Internal Scans
- Results from scans executed through the cloud platform
- Requires selection of an internal proxy for retesting
- Maintains consistent access to internal targets
-
Uploaded Local Scan Results
- Support for results from locally executed scans
- Requires proxy host with access to the original internal targets
- Seamless integration with existing internal scanning workflows
To set up internal scanning capabilities and configure proxies, refer to our Internal Network Scanning guide. This covers both TunnelX setup for cloud-managed scanning and local scanning configurations.
For internal vulnerabilities, you’ll need a properly configured proxy. You can either:
- Use TunnelX for cloud-managed scanning (recommended for Enterprise users)
- Set up local scanning with result uploads Learn more in our Internal Scanning guide.